Introduction
According to reports from Risk-based security, during the first six months of 2023, there were more than 5,000 breaches reported on 7.9 million data exposed. It was 33.3% higher than in 2023 and records exposed also doubled by 112%.
We live in an Internet-driven world that makes our life comfortable. But at the same time, it poses serious computer security threats that can be nerve-wracking to solve. It sounds like real trouble. So, getting yourself educated on computer security concepts and fundamentals can help you face and solve unexpected threats you encounter at any time. Also, it helps detect the vulnerabilities in your security system and take measures to safeguard your data against cyber-attacks.
Besides, experts suggest that being aware of computer security is a a good way to safeguard your system and data integrity.
The following blog post discusses:
- What is computer security? (Computer security definition)
- Types of computer security
- Why consider learning computer security (cyber security)?
- What are the career opportunities in computer security?
So, let us get started by briefly understanding the concept of computer security that will enhance our vision to perceive it better in 2023.
Computer Security Definition & Its Types
What is computer security? In simple terms, computer security is safeguarding your system from any unrecognized access, theft, or intrusion. For instance, when you use a firewall, it spots and prevents unauthorized entry into your computer network.
Depending on the purpose, computer security gets categorized into the following types:
- Information security
- Network security
- Application security
- Internet security
- Cyber security
Hence, Computer security can be defined as controls that are implemented to ensure the confidentiality, integrity, and availability of all computer components. Now, further elaborate lets learn about security types.
Cyber Security Training & Certification
- Detailed Coverage
- Best-in-class Content
- Prepared by Industry leaders
- Latest Technology Covered
Computer Security Types
There are different kinds of computer security that are widely used to protect an organization's valuable information against the finest cyber threats. Below are the top 5 security types that assist in protecting valuable information.
1. Information security
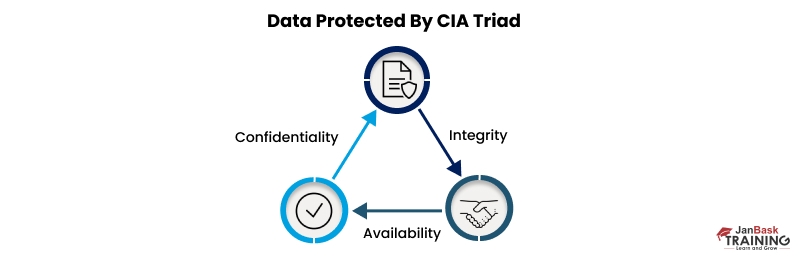
This popular CIA Triad security model is the starting point of any organization’s security that abides by the three principles - confidentiality, integrity, and availability. It is a traditional security form that has been in existence for several decades.
Confidentiality - This security principle states that only authorized people can access or modify any information or operation. For instance, entering a password while operating your debit cards at any ATM is an authentication to the access of sensitive information that ensures confidentiality. The best countermeasures to retain confidentiality are data encryptions and labeling, good access controls, and powerful authentication mechanisms.
Integrity - Maintains data authenticity and resists any unauthorized data modifications. For instance, the bank software provides data integrity of all transaction records of a user account. The best practices to maintain integrity are digital signatures, encryption, and hashing.
Availability - Any time access to authorized persons. For example, with a debit card and its associated PIN, you have 24/7 access and availability of ATM services. The use of hardware fault-tolerant servers is the best way to maintain the availability principle.
2. Network security
According to Statista, Trojans account for 58% of all computer malware, and as per Cloudflare, there was a 175% increase in DDoS attacks in the fourth quarter of 2023.
This computer security model consists of hardware and software technologies to prevent unauthorized access to the system and network, which helps maintain data integrity and usability.
Some types of network security protections include
- Next-Generation Firewalls - These have inbuilt security protocols to check the network traffic both ways. The next-gen firewall blocks out not-so-desirable traffic and prevents the possibility of an application layer or a malware attack.
- Remote access VPN - It is an effective way to protect the computer network for people accessing it via extranet, mobiles, and telecommuters. Encryption, data scanning, and multi-factor authentication are a few ways to ensure data privacy via VPNs.
- Zero Trust Network Access (ZTNA) is a standard security method that emphasizes providing the required user access that is enough to perform their job roles.
- Data Loss Prevention (DLP) - It is a computer security model that clubs technology and cybersecurity techniques to safeguard any sensitive organization’s data from being exposed.
- Cloud-Network Security - It is a popular data center premise that holds and protects tons of data from the applications using a Software-defined Networking/Wide Area Network.
These offer a shield against malware attacks like trojans, virus, worms, trojans, and adware. A small brief on these common cybersecurity threats can help to comprehend better:
Adware - It is a common type of malware displayed on the ad on your laptops and mobiles and does not cause a high degree of danger.
Worms - A self-replicating program that swallows the OS files until all the information on the system gets emptied.
Virus - A piece of infected code/program that attaches itself to another program to procreate multiple times that gets transmitted during a file or a software share.
Trojans - It is malware disguising itself as legit software to pull out sensitive financial information from computers.
3. Application security
Application security is the process of safeguarding applications from outside security threats by using the related hardware and software design in the development phase.
With application security, all the malicious activities on the platform get minimized, which helps prevent any data access or modifications by hackers.
For instance, a firewall installed in a software application determines the file handling and execution procedures, a countermeasure against undefined file executions in that application. As far as hardware is concerned, Routers is the best way to stay invisible with the IP addresses searched for on that particular computer.
Some other instances of application security tools are biometric systems, antivirus software, encryption and decryption programs, and spyware detection programs.
4. Internet security
According to Cybersecurity ventures, there will be a ransomware attack per 11 seconds in 2023, and in comparison to their previous analysis, it is a rise 0f 20% from 2019, which was 14 attacks per second.
To prevent such attacks, Internet security abides by particular protocols to ensure protection from viruses, hacking, malware, and DDoS attacks, i.e when an e-commerce site uses security measures like Multi-factor authentication it signals trustworthiness for its customer base to navigate and engage in a business transaction.
5. Information Technology Security
According to Verizon, 43% of cyber attacks gets aimed at small businesses. But only 14% are ready with a security system.
IT security refers to the activities, processes, and best practices protecting networks, information, or devices from unidentified access. The three areas that encompass IT security is - cloud security, endpoint security, and cybersecurity.
- Endpoint security - It is the act of safeguarding all the network endpoints like mobiles, PCs, and laptops from malicious activities.
- Cybersecurity - It is the process of protecting networks, computers, information, and gadgets against any threats.
- Cloud security - As the name suggests, it is a set of strategies designed to safeguard the cloud environment against any cyberattack.
As you can witness, whatever the security protocol the companies or individuals deploy, hackers find a loophole to break into your system. Thus, it compels large corporations to hire seasoned computer security professionals to ensure confidentiality and integrity and safeguard their reputations. It, in turn, opens job opportunities for many.
These job opportunities are an ingenious reason to study cybersecurity and pursue a promising career. Besides, there are some highly-attractive benefits that let you consider cybersecurity as a career option.
Let us dive into the subsequent section for more insights.
Why Learn Cyber Security?
With open doors of opportunities, many have started opting for a Cybersecurity career. But a few are still skeptical about a career choice in it. So, the following section of the benefits list will clear second thoughts about this profession choice.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
1. Payscale is high
With cyberattacks soaring, many corporate companies, government bodies, and businesses try to level up their security measures by employing proficient computer security professionals. They are ready enough to invest in their training programs as well. Besides, due to the shortage of skills, they are open to offering lucrative salaries for deserving candidates.
Few stats on salaries is a testimony of how a career and a payscale in Cybersecurity are impressive:
As per Glassdoor, the yearly salary of computer security professionals looks like this:
- The average salary of a cybersecurity engineer is $1,01,548 and the lowest, earns $71, 162
- Cyber security analysts earn around $80,078 with years of experience
- The Network security architect's salary is $1,26,981

These payscale and Glassdoor figures are impressive. Besides, you can make your cybersecurity salary soar high with professional guidance from a mentor or career coach when you enroll for certification and upgrade your skill set.
2. Giant Tech Companies Hire Computer Security Experts
Do you know that the world is witnessing a shortage of skilled computer security professionals, and more than half of the job openings remain unfilled for weeks or even months?
The following is a list of tech companies that offer cybersecurity jobs.
1. Sophos
They offer computer security services like data encryption and advanced data security. This next-gen company is a proud AWS partner.
At present, they have openings for the following positions:
- DevOps cloud engineer
- Security architect
- Senior data scientist
2. Google, Amazon, IBM, and Microsoft - Cloud Storage Providers
With more and more corporate companies migrating to the online cloud platform, they look for professionals who can effectively handle their sensitive data. A few big names in cloud computing like Google, IBM, Microsoft, and Amazon need computer security personnel.
You can now apply for the following openings:
- Security solutions engineer (Google Cloud)
- Cyber security architect (IBM)
- Principal security Ops engineering manager (Microsoft)
- System development engineer
3. Check Point Software Technologies
They provide identity and access management, solutions for multi-cloud systems, and cloud services. The company has partnered with Google and AWS to offer their clients on-premises network solutions.
You can send in your resume for the following cyber security jobs,
- Cloud security engineer/architect
- Security engineer/architect
Not only this, numerous computer security jobs are awaiting you at
- Intel
- Apple
- Patient First
- Federal Reserve Bank of New York
- CyberArk
- General Motors
- Cisco
3. Work in Diverse Industries
Once, defense contractors and government agencies were the mainstream job providers for cybersecurity professionals. But, now things have changed radically. With exponential growth in technology like Automation, Cloud computing, IoT, big data, and AI, we have started to live in a data-driven era.
With tons of online data being sent and received, organizations are well aware of data breaches and thus feel the need to step up their security measures. They look out for professionals who can safeguard their data integrity and accessibility.
The undermentioned are a few industries that require computer security experts:
- Finance
- Health care
- Manufacturing
- Retail
- Food
- Education
With numerous jobs available at top companies that provide higher compensation for entry-level positions, a career path in cyber security apparently become a reckoning choice of many.
After deciding upon a cybersecurity career, the next step is to have insights into how the career opportunities of this wing are likely to be in the future. The subsequent section provides the required information.
Cyber Security Career Opportunities
As there is a skill gap in this sector, experts predict the job growth rate is to soar by the end of this decade. So, let us start with a few stats that can motivate you to step into this high-profile industry.
- As per the Bureau of Labour Statistics, information security job growth gets projected at 37% by 2025. Also, they have stated that this job role will be among the top 10 fastest-growing occupations over the next decade.
- According to Emsi, a labor market analytics company, Application dev security, and Cloud security are the fastest-growing areas in cyber security, with a projected growth of 164% in the last five years.
- According to a cybersecurity ventures report, the spending on the security industry is to raise $170.4 million in 2023, which is a leap from $124 million in 2023.
So, it is time to look at how to start your career in cybersecurity.
You can follow the steps listed below to acquire computer security jobs.
Career Path: How to Start Learning Cyber Security?
If you are planning to start a career in the cybersecurity profession, you have to keep updating your technical skills. Even though the skill-building process is challenging, with the following tips, it is possible.
Start with a Cybersecurity Course for Beginners.
A beginner-friendly cybersecurity course helps you get the foundation in the right environment. It helps analyze whether the cybersecurity profession aligns with your skillsets and career objectives.
Enroll Yourself in a Cybersecurity Course
After a skillset analysis, the next tip on the list is to search for a cybersecurity training program that helps you prepare for the certification. While choosing a cybersecurity training program, ensure whether they have industry-expert-led training, an updated course curriculum, flexible timings for training sessions, capstone projects, sufficient e-learning resources, and career counseling after course completion.
Cyber Security Training & Certification
- Personalized Free Consultation
- Access to Our Learning Management System
- Access to Our Course Curriculum
- Be a Part of Our Free Demo Class
Prep to Acquire your Cybersecurity Certifications
Work on ethical hacking - Enrolling in a cybersecurity training course will guide you through the process of practicing ethical hacking. The mentors will assist you in choosing a suitable set of tools and techniques to make you gain expertise.
Real-time training at virtual labs - Nothing beats the experience of using the security techniques, tools, and skills in a virtual environment that cybersecurity courses offer. This type of learning helps you hone your technical skills.
Earn certification - With proper training and real-time practice, it is possible to clear certifications that add more value to your resume during the job search process. When you have credentials, it highlights you as a competitive candidate than the rest. In simple words, you can utilize the skill gap trend in the industry by showcasing your professionalism.
A list of In-demand Cybersecurity Certifications for your reference:
- Certified Ethical Hacker (CEH)
- CompTIA Security+
- Certified Information Security Manager (CISM)
- Certified Information Security Professional (CISSP)
- Cisco Certified Network Associate (CCNA) Security
Improve your Technical Skills
With more enterprises shifting towards cloud storage, there is room for digital data transmission. Thus they need experts who can protect their confidential data. Being said that, playing the role of computer security expert requires a unique technical skillset.
What are they? We have jotted down a few technical skills that get you into the cybersecurity industry.
- A deep understanding of operating systems like Mac, Linux, Kali Linux, and Windows is essential for penetration testing and ethical hacking.
- Getting your hands-on networking will help your data transmission process.
- Also, acquiring system administration knowledge makes your computer configuration and maintenance activities hassle-free.
- As a cybersecurity expert knowing the ins and outs of firewalls, routers, and computer network are mandatory.
- Gaining coding expertise is not essential for this domain. But being knowledgeable in a few programming languages like JavaScript, C, C++, Python, HTML, SQL, and PHP can render you a successful career.
- Go ahead and equip yourself with technologies related to cloud computing platforms.
- The last technical skill on our list includes IoT, Blockchain, and AI. When you train yourself with these future technologies, it helps you stay ahead of the rest.
Work on your soft skills
Non-technical skills is also essential to excel in this career path. The undermentioned are a few ones that you can work upon during your cybersecurity training sessions.
The computer security job role is no less of an adventure. Therefore you have to possess high-level problem-solving skills to face and solve new challenges daily on your work front.
Cybersecurity professionals have to work and communicate with other departments regarding cybersecurity policies and strategies. Owning efficient communication skills enables you to explain the technical aspects in simple terms.
The IT world keeps evolving and cyber security is no exception. So, computer security experts have to keep themselves open to learning the latest technologies and trends to implement the best security practices in their organizations.
Join the online community
- LinkedIn Groups like CISO
- Private forums like Advanced Persistent Threats (APT) and Wilders Security
- Cyber Intelligence Network
- IEEE Cybersecurity Community
- ISACA Engage
- IET Cyber Security Community
These are a few. You can find out the cybersecurity worker groups and associations in your town/city that conducts a monthly meeting to keep themselves updated. These communities have experts who are ready to answer your questions happily. So, having great contacts is beneficial for you in the future.
Access Credible Resources
You can read informative blogs, white papers, and case studies and watch YouTube videos of Janbask training to have insights into Cybersecurity concepts. These learning sources can help you procure a Cybersecurity career path.
Wrapping Up
As you can see, none of the organizations want to lose their sensitive information but, at the same time, want to carry on with their services or processes without any security threat. So, they need professionals who can handle it with proficiency.
But with the skill gap existing in the industry for more than a decade, it has opened up career opportunities for aspirant job seekers. If you want to take advantage of the current situation, a cybersecurity certification from Janbask training can help you get started.
With Industry-mentors-led virtual classes, you get best-in-class online training programs that will provide insights into how to handle real-time breaches. Our expert training sessions hone your skillsets to clear your certification exams and job interview.
If you are interested to know about cybersecurity certification for beginners, or if you want to know how to become cyber security expert, get in touch with us.
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
8 days 02 Aug 2024
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
12 days 06 Aug 2024
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
0 day 25 Jul 2024
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
15 days 09 Aug 2024
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
1 day 26 Jul 2024
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
8 days 02 Aug 2024
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
2 days 27 Jul 2024
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
8 days 02 Aug 2024
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
2 days 27 Jul 2024
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
16 days 10 Aug 2024
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
29 days 23 Aug 2024
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
8 days 02 Aug 2024