Introduction
Simply put, a cybersecurity threat, also known as a cyber threat, signifies an attempt by a hacker or malicious actor to gain unauthorized access to a network with the intention of launching a cyberattack. These types of Cyberattacks incur substantial costs for both individuals and organizations affected by them. As per the FBI Internet Crime Report of 2024, these attacks resulted in a significant $10.2 billion in financial losses. This figure is projected to rise, highlighting the ongoing and growing threat of cybercrime.
This is the reason why top recruiters are in dire need of highly skilled cybersecurity professionals. The Washington Post states that there are over 36,000 unfilled cybersecurity positions in the public sector, while Cyberseek reports a staggering 597,000 job openings in cybersecurity across the private sector. This suggests that now is possibly the ideal moment to pursue Cybersecurity Certification training or start a career in this field and earn an impressive package.
Cyber Security Training & Certification
- Detailed Coverage
- Best-in-class Content
- Prepared by Industry leaders
- Latest Technology Covered
Different Types Of Cyber Threats & Why It’s CrucialTo Correctly Identify Them
Cyber threats vary widely, from overt examples like an email promising money in exchange for your bank details from a foreign leader to subtle threats such as malicious code that bypasses defenses and remains dormant on a network for extended periods, eventually causing expensive data breaches. As cyberspace becomes more intricate and comprehensive, the likelihood of encountering common cybersecurity threats increases.
With countless devices connected to various endpoints, maintaining security has emerged as a pressing challenge for business owners, as these security breaches are often the root cause of cyberattacks. As of 2025, cybersecurity attacks were evidently on the rise. Astonishingly, three out of four organizations have fallen victim to ransomware attacks, marking a 61% increase since 2020. The financial impact is significant, with an average hourly downtime cost of $250,000 from ransomware attacks.
To mitigate such risks, individuals and organizations must know how to prevent cyber attacks and for that, it’s critical to understand the different types of cyber-attacks and implement the necessary precautions. The greater the awareness among security teams and employees regarding various types of cybersecurity threats, the more proficiently they can prevent, prepare for, and respond to cyberattacks. So, let’s help you enhance your knowledge, identify potential threats, and proactively safeguard devices and data.
Types of Cyber Attacks You Must Look Out For
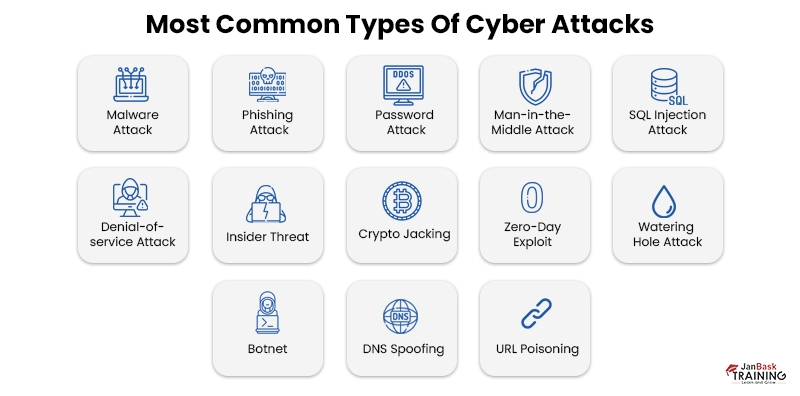
There are a number of common Cyber Security threats that take place globally. If you know these types of cyber attack examples, it’ll be easier for you to protect your networks and systems from them. Let’s examine in detail some of the most popular types of cyber attacks that can impact you or a huge business, based on their scale. Knowledge of these types will give you a direction on how to prevent cyber attacks and stay protected.

1. Malware Attack
Malware attack is the most common type of Cyber Security threats examples. The term ‘Malware’ refers to malicious software like spyware, ransomware, adware, or trojans that are specifically created so as to disrupt the working of a system by destroying data.
Trojans disguise themselves like legit software. Ransomware denies access to the network’s major components, while Spyware is software that steals essential and confidential data without your knowledge. Adware is also software that shows content related to advertising, like banners on users' screens.
Malware breaks into a network using a vulnerability, and when any user clicks on a malicious link, it downloads any dangerous email attachments or malicious content when an infected pen drive is used.
How to prevent a malware Attack -
- Use antivirus software - By using antivirus software like Norton, McAfee, Avast, etc., you can protect your system from a malware attack.
- Use firewalls - Firewalls help in filtering the traffic entering your device, which helps in protecting your system from malware.
- Avoid clicking on suspicious links- Be cautious and refrain from clicking on links in unsolicited emails, messages, or unfamiliar websites, as these can lead to malware infections.
- Regularly update your operating system- Ensure that your operating system is always up to date with the latest security patches and updates to protect against vulnerabilities and malware.
2. Phishing Attack
Phishing and pharming attacks are also highly widespread types of attacks in Cyber Security. Phishing is a type of social engineering attack where a cyberattacker pretends to be a legitimate contact and sends fake emails to the victim.
Since the victim is unaware of this, opens the email attachment and clicks on the malicious link. In doing so, the attacker gains access to sensitive information and account credentials. Cyber attackers can deploy malware using a phishing attack.

The Phishing Attack Circuit:
- Impersonation of a trusted source
- Disseminating messages through various channels
- Some recipients trust the message and interact with it
- Users visit a fake website and provide their personal information
- The attacker collects the data and exploits it for malicious activities
Outcomes:
- Bank account theft
- Credit card fraud
- Sale of personal information
- Identity theft
- Fraudulent schemes
- Distribution of advertisements
How to prevent a phishing Attack -
- Always verify the emails that you receive. Most phishing emails contain prominent errors such as spelling mistakes and formatting errors.
- Use anti-phishing toolbars.
- Always update your passwords.
Many well-known institutions and academic programs have started offering fundamental to advanced level CyberSecurity Training Online Courses, including CyberSecurity Training Certifications for students as well as professionals who have the required knowledge and aptitude for this subject, like JanBask Training. A CyberSecurity fundamental level program may help in better educating students to face today's competent cybercriminals, given the rapid evolution of technology and the fluid nature of cybercrime.
Another intelligent alternative is to attend an online cyber security course. Taking an online CyberSecurity Course to gain practical experience. To be a successful cybersecurity professional, you need to follow a proper Cybersecurity Certification Path, which contains everything like what cybersecurity certification is, its scope, different certifications, and much more…
3. Password Attack
This is one of the types of cyber attacks where an attacker cracks your password using different programs and password-cracking devices. Brute force attacks and keylogger attacks are some of the types of password attacks.
How to prevent Password Attacks-
- Always use a strong password.
- Avoid using the same password for multiple accounts.
- Always update your password.
4. Man-in-the-Middle Attack
MITM, i.e., Man-in-the-Middle Attack, is also referred to as an eavesdropping attack wherein an attacker comes in between a two-party communication. In simple words, in this type of attack, the attacker hijacks a session between a client and host and after this, the attacker steals and manipulates the data. The client-server communication cuts off, and instead of that, the communication line goes through the attacker.
How to prevent Man-in-the-Middle Attack -
- Use encryption on your system and be careful about the security of the website you’re using.
- Avoid using public Wi-fi networks.
5. SQL Injection Attack
SQL, i.e., Structured Query Language injection attack, is performed on database-driven websites wherein an attacker manipulates the standard SQL query by injecting a malicious code into an insecure website’s search box to make the server reveal confidential information. Because of this, the hacker can view, modify and delete database tables. Cyber attackers may get administrative rights using this.

How an SQL Injection Works:
- An attacker detects a vulnerable website that relies on SQL and inserts a malicious SQL query through input data.
- The database validates the malicious query and executes the command.
- The attacker gains access to view and modify records and may even obtain administrative control over the database
How to prevent SQL Injection Attack
- Use an intrusion detection system that detects unauthorized access to a network.
- Check the authenticity of user-supplied data, which helps to keep user input in check.
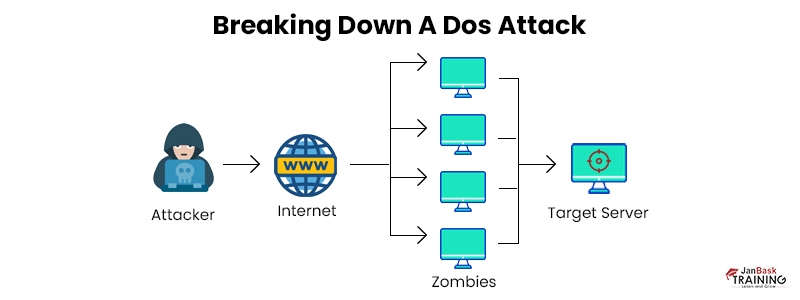
6. Denial-of-Service Attack

A Denial-of-Service attack is a severe danger to businesses where cyber attackers target computer systems, servers, or networks and fill them with unwanted traffic in order to use up their resources as well as bandwidth.
In case of such security attacks in network security, it becomes difficult for the servers to manage the incoming requests, eventually slowing down the website that it hosts. It also neglects authentic service requests.
This network security attack is also known as Distributed Denial-of-Service (DDoS) attack when cyber threat attackers utilize several compromised systems so as to initiate the attack.
How to Prevent Denial-of-Service Attack
- By running a traffic analysis, identify malicious traffic.
- Recognize the warning signs such as network slowdown, intermittent website shutdowns, etc., and also take the required steps immediately during such events.
- Develop a proper incident response plan, maintain a checklist, and ensure that your team and data center can handle a DDoS attack.
7. Insider Threat
From the title, an insider threat doesn’t involve a 3rd party but an insider. In situations like this, it might be a person from inside the organization who might know everything about the organization. This one of the top Cyber Security threats can result in tremendous damage. These types of cybersecurity attacks can result in tremendous damage.
In small organizations, insider threats are uncontrollable as the employee there holds access to several accounts with confidential information. There are many reasons behind these threats - it could be greed, ill feeling, or even negligence. Insider threats are difficult to predict; that’s why they’re tricky.
How to Prevent Insider Threats
- Organizations should have a good culture of security awareness.
- Companies must limit the IT resources that staff can access based on their job roles.
- Organizations must train employees to spot insider threats. This will help employees understand when a hacker has manipulated or is attempting to misuse the organization's data.
8. Crypto Jacking
This term is closely associated with cryptocurrency. It occurs when cyber attackers access someone else’s device for cryptocurrency mining. The cyber attackers gain unauthorized access by infecting victims' websites or by manipulating the target user to click on a harmful link. For carrying out crypto-jacking, the attackers can take the help of JavaScript code ads, and the target users are not aware that crypto-mining code is working in the background, and the only sign to witness crypto-jacking can be a delay in the execution.

Functioning of Cryptojacking
- You click on a seemingly harmless link in an email.
- The link appears innocent but contains cryptomining code.
- Clicking the link loads the crypto mining code onto your computer, running a mining script in the background.
- The script takes control of your computer's processing power.
- The script uses part or all of your device's computing power to mine cryptocurrency.
- The cryptojacker tracks the mined cryptocurrency and collects it in their digital wallet.
How to prevent Crypto-jacking
- Always keep your software and all the security apps updated because crypto jacking mainly infects unprotected devices
- Arrange crypto jacking awareness training programs for your employees, which will help them identify crypto jacking.
- Install ad blockers on your systems since ads are the primary source of crypto jacking threats. To detect and block crypto mining scripts install extensions like MinerBlock.
9. Zero-Day Exploit
A Zero-day exploit can take place following the announcement of a network vulnerability, and in most cases, the vulnerability is difficult to resolve. Therefore the vendor detects it, thereby users get aware of it.
Also, based on the vulnerability, the developer might take unpredictable time to resolve the issue. In the meantime, cyber security attackers can target exposed vulnerabilities.
The malicious attackers ensure to exploit the vulnerabilities even before a security patch or solution is implemented for it.
How to prevent Zero-day exploits:
- Organizations must implement fluent patch management processes and can use governance solutions to automatize the procedures. Which will accelerate the deployment.
- Organizations must have an incident response plan in order to handle cyberattacks. Also, maintain a proper strategy to focus on zero-day exploits. This way, minimizing or altogether avoiding the damage is possible.
10. Watering Hole Attack
In a watering hole attack, the victim is a specific group of businesses or regions. During this attack, the cybersecurity attackers target websites that the targeted group commonly uses. These websites are detected either by cautiously monitoring the specific group or just by guesswork.
Following this, the malicious cyber attackers infect these targeted websites using malware, and it then infects the victim’s system/(s). In this type of attack, the cyber attackers target the victim’s personal information. It’s also possible that the attacker can take remote access to the infected system/(s).
How to prevent Watering Hole Attack
- Regularly update your software and minimize the chances of a cyber attacker exploiting vulnerabilities. Ensure that you regularly check for security patches.
- For detecting watering hole attacks, use your network security tools. You can use IPS (Intrusion Prevention Systems) to identify such types of suspicious operations.
- It’s recommended that you conceal all your online operations to prevent watering hole attacks. For that, always use a VPN and also make good use of the private browsing features of your browser.
- A VPN helps in providing a secure connection with other networks over the web. It acts as a shield to all your browsing activities.
All of those were the top 10 types of cyber attacks you should be aware of in [2022-23]. Now in the coming section, we’ll walk you through how to prevent different types of attacks in Cyber Security.
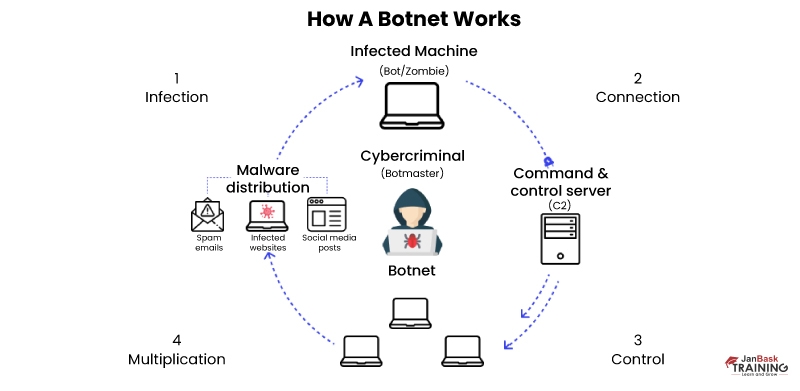
11. Botnet
Botnets contain a group of web-connected computer systems and devices that are invaded and manipulated remotely by cyber attackers. In order to maximize the size and power of botnets, vulnerable IoT devices can also be used by cybercriminals. These devices are frequently used for email spam, click fraud campaigns, and create unwanted traffic for DDoS cyber attacks.

How to prevent Botnet Attacks
- Always keep your software up to date.
- Keep a close tab on your monitor.
- Keep a watchful eye on failed login attempts.
- Install advanced botnet detection software.
12. DNS Spoofing
CyberSecurity attackers have long used DNS vulnerabilities to alter the IP addresses stored on DNS servers and resolvers using fake entries so that the targeted user can be redirected to a fake website that is controlled by the hacker rather than to a legitimate website. The fake websites are designed to resemble the legitimate site the victim was trying to visit. Hence they aren’t suspicious when the victim is asked to enter login credentials to what the victim thinks is an authentic website.
How to prevent DNS Spoofing
- Filter your DNS server.
- Check if the legitimate NameServer matches what is locally resolved.
13. URL Poisoning
A website URL is a distinct identifier required to detect a resource on the web and tell the web browser how and where to retrieve it. Cyber attackers can easily modify a URL so as to gain access to a victim’s personal information or resources to which they mustn’t have access.
For instance, if an attacker gains access to a victim’s account at xyz.com and can view the victim’s account settings: https://www.xyz.com/acount?user=7248 and easily change this existing URL to https://www.xyz.com/acount?user=1337 to check whether they can access the account settings of user 1337. Now, if the web server of xyz.com doesn’t check if every user has legitimate authority to access the needed resources, specifically, if it contains user-provided inputs, then the attacker can see the account settings of user 1337 and might of every other user.
URL poisoning is carried out to collect personal information such as usernames, files, and database data or to access administration pages required to control the complete website. If the hacker does manage to gain access to privileged information by manipulating the URL, it’s called Insecure Direct Object Reference.
How to prevent URL Poisoning
- Fortunately, an antidote: DNS Security Protocol (DNSSEC), is available, which was developed specifically to counter DNS poisoning.
- Undoubtedly, the CyberSecurity job market will be in demand and will continue to grow in future years. As there is a number of sub-disciplines, it’s not easy to point out one specific technical skill that needs to be acquired. But having said that, each of these disciplines has a CyberSecurity component, which is worth noting.
Most in-demand certifications in the CyberSecurity domain include-
- CEH -Certified Ethical Hacker.
- OSCP-Offensive Security Certified Professional.
- CISA – Certified Information Security Auditor.
- GCIH (GIAC Certified Incident Handler)
- CISSP – Certified Information Systems Security Professional.
- CISSP-ISSAP (Certified Information Systems Security Architecture Professional)
- CISSP-ISSEP Information Systems Security Engineering Professional.
- CISSP-ISSMP Information Systems Security Management Professional.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
Other Types Of Cyber Attacks You Must Be Aware Off
14. Spoofing
It is a technique used to impersonate someone or something else in order to exploit vulnerabilities or trick individuals into revealing sensitive information.
15. Identity-Based Attacks
Using someone else's PIN to get into their systems and gain illegal access to their data in order to steal or modify their personal information is known as identity-based attacks.
16. Code Injection Attacks
In this technique data manipulation is performed by introducing malicious code into a software program. For instance, to steal data, the attacker inserts malicious code into a SQL database.
17. Supply Chain Attacks
The attacker exploits loopholes in the hardware or software supply chain to gather private data.
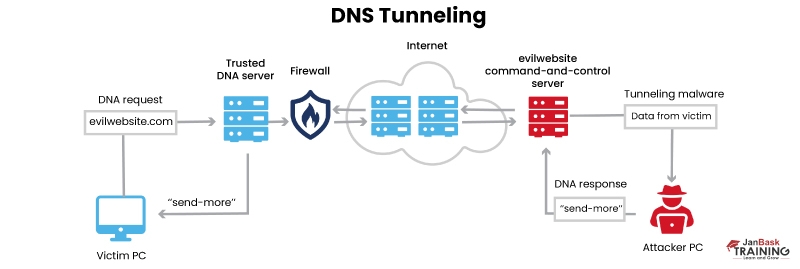
18. DNS Tunneling
The attacker uses the Domain Name System (DNS) to go around security measures and communicate with a server located remotely.

19. IoT-Based Attacks
The attacker takes advantage of weaknesses in Internet of Things (IoT) devices, such as smart thermostats and security cameras, to steal information.
20. Ransomware
Ransomware is a type of cyberattack where malicious software is used to encrypt files on a victim's computer or network, rendering them inaccessible until a ransom is paid.
21. Distributed Denial of Service (DDos) Attacks
Here attackers flood a website with traffic to block legitimate users from accessing it and to take advantage of network weaknesses.
22. Spamming
In this type of cyber attacks the attacker sends spam messages and emails to trap people similar to phishing scams.
23. Corporate Account Takeover (CATO)
Here in this technique the hackers use stolen credentials of individuals to access their bank accounts.
24. ATM Cash Out
In order to use ATMs to make big cash withdrawals, hackers get close to a bank's computer systems.
25. Whale-Phishing Attacks
Using advanced social engineering techniques, hackers target high-profile individuals such as CEOs or celebrities to obtain sensitive information.
26. Spear-Phishing Attacks
In this technique the attackers target particular members of an organization or groups. They exploit social engineering strategies for stealing private data.
27. Session Hijacking
To authenticate the user's session with a web application and take over the user's session, the hacker gets access to the user's session ID.
28. Brute Force Attack
A hacker gets access to a system without authorization by trying multiple passwords until they find the right one. It has a great deal of potential against weak passwords.
29. Web Attacks
Here the attacker uses cross-site scripting (XSS), SQL injection, and file inclusion to attack websites.
30. Trojan Horses
A type of harmful software that pretends to be a genuine program, but secretly carries harmful code. When it gets installed, it can do bad things like stealing information and taking control of the computer.
31. Drive-by Attacks
By accessing its infected website, the user's computer gets infected with malware that is secretly inserted into other programs without the user's awareness.
32. Cross-Site Scripting (XSS) Attacks
In order to gain access to the user's information and steal sensitive data like the user's passwords and credit card numbers, the attacker inserts unauthorized code into a genuine website.
33. Eavesdropping Attacks
To obtain sensitive information, a hacker intercepts communications between two parties.
34. Birthday Attack
In a cryptographic attack called the birthday paradox, the attacker takes advantage of the fact that it's easier than expected to find two inputs that produce the same output in a hash function. By doing this, the attacker can compromise the security measures in place and gain unauthorized access.
35. Volume-Based Attacks
To prevent genuine users from accessing a system, the attacker takes over it with large amounts of data. Consider DDoS assaults, in which a number of compromised machines attack a particular website with bandwidth in an effort to bring it down.
36. Protocol Attacks
The attacker exploits flaws in network protocols to break into a system or interfere with its normal operation.
37. Application Layer Attacks
In this type of cyber attack, the hacker attempts to take advantage of loopholes in applications or web servers by focusing on the application layer of a system.
38. Dictionary Attacks
The attacker uses a list of common terms to try and guess a user's password. This attack is successful because so many people choose simple or weak passwords.
39. Virus
Corrupt software has the ability to reproduce and propagate to other systems. Viruses can seriously harm computer systems, corrupt files, steal data, and do other things as well.
40. Worm
Worms replicate and spread to other computers, but they don't require human involvement like viruses do.
41. Backdoors
Due to this weakness, attackers are able to access a system or network without authorization by evading normal authentication protocols.
42. Bots
These software packages automate network or internet tasks. They can be employed for bad things like Distributed Denial of Service (DDoS) assaults.
43. Business Email Compromise (BEC)
In order to deceive the victim into sending money or private information to the attacker, the attackers pose as a reliable source. It uses email to target companies and organizations.
44. Cross-Site Scripting (XSS) Attacks
In this technique, the hacker introduces malicious code into a vulnerable website that targets web applications in order to steal sensitive data or launch unauthorized attacks
45. AI-Powered Attacks
Utilizes machine learning and artificial intelligence to get around conventional security measures.
46. Rootkits
It gives attackers privileged access to the victim's computer system.Rootkits can be difficult to detect and remove, and they can be used to conceal other forms of malware like spyware or keyloggers.
47. Spyware
Spyware is malicious software that gathers private data from a victim's computer. Passwords, credit card numbers, and other private information fall under this category.
48. Social Engineering
This is a trick used by cybercriminals to get users to provide sensitive information or take acts against their better judgment.
49. Keylogger
It is malware that records keystrokes that a victim types into their computer. Passwords, credit card numbers, and other private information fall under this category.
50. Emotet
This malware is made to steal sensitive data and spread it through a network of computers. Emotet may be exceedingly challenging to find and uninstall and is frequently propagated through phishing emails.
Although it can be inconvenient and disruptive, adware generally poses less of a threat than other forms of malware.
52. Fileless Malware
This kind of malware does not rely on files to infect a victim's computer system. Instead, fileless malware uses the system's built-in resources, such as memory or registry keys, to run malicious code.
53. Angler Phishing Attacks
Use customized emails that are highly targeted to reach people or organizations. Angler phishing attempts are frequently successful in collecting critical information despite being difficult to spot.
54. Advanced Persistent Threat (APT)
An Advanced Persistent Threat (APT) attack is when an attacker gains ongoing and continuous access to a victim's computer system for a long time. These attacks are very advanced and hard to notice or remove because they are highly sophisticated.
All of those were the top 50+ types of cyber attack examples you should be aware of in 2024 and ahead. Now, in the coming section, we’ll walk you through the several Certifications on cybersecurity and how to prevent different types of attacks in Cyber Security.
Professional Certification for a Cyber Security Career
As discussed, there are different types of Cybersecurity threats. We have gone through 50+ cyber attacks examples. To overcome them, there’s a raving demand for CyberSecurity professionals around the world. Also, endless possibilities are awaiting you in the CyberSecurity sector. To be a CyberSecurity professional, you need to acquire the right cybersecurity skills, cybersecurity tools, and best practices.
You can start your career with our Cyber Security Courses Online by JanBask Training, which allows you to gain fundamental to advanced CyberSecurity skills and techniques to defend against cyber threats. After this course, you’ll be equipped with all the skills needed to become an expert in this rapidly growing sector. With this best-in-class program, you’ll also learn comprehensive approaches to securing your infrastructure, safeguarding your data and information, running risk analysis and mitigation, achieving compliance, and much more.
How can We Prevent CyberSecurity Attacks Altogether?
Even though we’ve discussed numerous ways to prevent various types of Cyber attacks, why not review them and take a look at some of the crucial tips that can help you avoid various types of attacks in Cyber Security altogether-
- Regularly change your passwords and always use strong and alphanumeric passwords that aren’t easy to guess. Avoid using overly complicated passwords that you might forget. Most importantly, never use the same passwords twice.
- Regularly update your OS and applications. You can say that it's a primary prevention method for any type of CyberSecurity attack. It’ll help you eliminate vulnerabilities that cyber attackers try to exploit. Always use antivirus protection software that is trustworthy as well as legitimate.
- Always use firewalls and different network security tools like IPS (Intrusion Prevention Systems), Access control, Application security, etc.
- Prevent opening emails from unknown senders. Examine the emails that you receive for inconsistencies and compelling errors.
- Always use a VPN which ensures that the traffic between your system and the VPN server is encrypted.
- Frequently back up your data. As specified by several security experts, having three copies on two distinct media types and one more copy in cloud storage is excellent. Thus, even in a cyber-attack, you can wipe out your computer system’s data and restore it again with the most recent backup.
- Make sure that the employees are aware of CyberSecurity principles. They should know the different types of cyberattacks and how to prevent them.
- Make use of 2-FA or Multi-Factor Authentication. When using a 2-FA, users need to provide 2 distinct authentication factors to verify them. But when the users are asked for more than 2 different authentication factors aside from their username and password, it's termed as Multi-Factor Authentication. It proves to be an essential factor for securing your account.
- Try not to use public Wi-Fi without a VPN.
- Also, secure your mobile devices. They can also be a cyberattack target. Always deploy software only from legal and trustworthy sources, and don’t forget to update your system/(s).
- Always keep your software up to date. And keep a close tab on your monitor.
- Keep a watchful eye on failed login attempts. And install advanced botnet detection software.
- Filter your DNS server. And check if the legitimate NameServer matches what is locally resolved.
Those were the crucial tips for you to deploy to secure your systems and networks from different types of attacks in Cyber Security.
Conclusion
You’ve understood everything about CyberSecurity attacks through this blog. You’ve understood what a CyberSecurity attack is. What are the different types of CyberSecurity attacks, and what are the different ways to avoid them?
As cyber crimes are increasingly growing today, it’s necessary to be aware of them and know how to secure networks. If you would like to learn more about cyber security, Visit our Cyber Security tutorial.
If you still have doubts concerning different types of CyberSecurity Courses, do mention them in the comments section below. Our experienced and skillful professionals will get back to you earliest!
Cyber Security Training & Certification
- Personalized Free Consultation
- Access to Our Learning Management System
- Access to Our Course Curriculum
- Be a Part of Our Free Demo Class
FAQs
Q1. What are your EC Council Accreditation - Cyber Security Training & Certification objectives?
JanBask Training’s EC Council Accreditation - Cyber Security Training & Certification offers fundamental level, intermediate and advanced -level CyberSecurity skills that are required for industry-leading certifications such as - CompTIA Security+, CEH, CISM, CISSP, and CCSP.
This course starts with fundamental level technical training and proceeds to intermediate level hacking techniques like reverse engineering, penetration testing, etc.
What are the benefits of JanBask Training’s EC Council Accreditation - Cyber Security Training & Certification?
JanBask Training’s EC Council Accreditation - Cyber Security Training & Certification course allows you to -
- Be well-informed about the latest CyberSecurity trends and ensure that you’re taking sufficient CyberSecurity measuring in your business.
- Prevent the chances of phishing attacks by sticking with legitimate security measures.
- Learning about legit needs, privacy policies, and auditing processes of your cloud environs.
- Focusing on aligning the IT infrastructure and deleting the litter by using appropriate software solutions and investing in a partner who can support you.
Q2. What are the career benefits of doing these CyberSecurity Courses Online?
Cybersecurity professionals should learn to develop a 360-degree view of the cybersecurity domain that comprises a wide array of security components and technologies. JanBask Training has bundled all of these critical skills into this EC Council Accreditation - Cyber Security Training & Certification program.
Its benefits are as follows:
- If you’re thinking of making Cybersecurity a career option in different roles like penetration tester, cybersecurity analyst, network analyst, cybersecurity auditor, cybersecurity architect, forensics investigator, and many more, then Cybersecurity is essential.
- According to Indeed, there are 40,000+ in the US.
- According to Glassdoor, the median salary for a cybersecurity analyst is $134,000 in the US.
Q4. What skills will I learn through EC Council Accreditation - Cyber Security Training & Certification course?
After completing this course, you’ll be armed with the following skillsets:
Installing, configuring, and implementing public key infrastructure and network components when assessing and troubleshooting different issues to help support your organization’s security.
Master advanced ethical hacking concepts in order to efficiently handle information security. Designing security architecture as well as a framework for a highly secure IT operation. Secure data transfer, plan disaster recovery, access CSP security, and manage customer databases.
Q5. Who can register for this program?
Our EC Council Accreditation - Cyber Security Training & Certification course is best suited for:
- All levels of IT auditor/penetration tester
- Security consultants/managers
- IT directors/managers/consultants
- Security auditors/architects
- Security systems engineers
- Chief information security officers (CISOs)
- Chief compliance/privacy/risk officers
- Network specialists, analysts, managers, architects, consultants or administrators
- Technical support engineers
- Systems analysts or administrators
Q6. Which courses and topics will your EC Council Accreditation - Cyber Security Training & Certification cover?
This course includes -
- Introduction to CyberSecurity,
- Footprinting & Reconnaissance,
- Scanning, Enumeration, Vulnerability analysis, and Malware threat,
- Social engineering, network, and system hacking
- Hacking, Blockchain & Cryptocurrency
- Testing, Security compliance & auditing
- What are the prerequisites for your EC Council Accreditation - Cyber Security Training & Certification?
Learners need to have an undergraduate degree or a high school diploma.
Q8. Which CyberSecurity job roles can I earn after the completion of this course?
You can earn the following best cyber security job roles-
- Cryptography Engineer
- Cybersecurity Manager
- Penetration Tester
- Security Engineer
- Information Security Analyst
- Digital Forensic Examiner
- Security Architect
- Security Systems Administrator
Q9. What is the Cybersecurity Online Course Admission Process?
The applicants must fill up the application form and submit it. The applicant must pass the entrance exam to get admission to the cyber security course online with the requisite score. After this, there will be reviewing and verification of shortlisted candidates. Once the payment is made, the shortlisted candidates will be enrolled in cyber security courses online.
Q10. What are the key features of your CyberSecurity Course Online?
Following are the key features of our CyberSecurity Course Online -
- Instructor-led interactive online sessions
- Course completion certification
- Access self-paced videos and webinars
- Lifetime access to study material
- 24*7 student support
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
6 days 25 Jul 2025
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
6 days 25 Jul 2025
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
4 days 23 Jul 2025
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
6 days 25 Jul 2025
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
6 days 25 Jul 2025
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
13 days 01 Aug 2025
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
-0 day 19 Jul 2025
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
7 days 26 Jul 2025
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
6 days 25 Jul 2025
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
9 days 28 Jul 2025
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
6 days 25 Jul 2025
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
7 days 26 Jul 2025


























Ali Price
I wanted to know what are the different types of CyberSecurity threats and how to prevent them and your post really helped me in understanding well.
JanbaskTraining
Hi, Glad to know that you found this post helpful! For more insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Eduardo Bennett
It’s a very informative blog, a must-read for people who want to be aware of the 13 most common CyberSecurity attacks
JanbaskTraining
Glad you found this useful! For more insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Fernando Wood
Hey, is there any separate guide you can help me prepare for CyberSecurity certification courses?
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here, and we will get back to you shortly!
Anderson Barnes
Earlier I thought that the job opportunities after graduation were not properly explained in a few places, and after reading this post, I got to know the different factors.
JanbaskTraining
Glad you found this useful! For more insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Angelo Ross
How to choose the best one among the numerous courses after graduation?
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here, and we will get back to you shortly!
Spencer Henderson
Can anyone with an undergraduate or high school diploma join the training? If yes, then whom to contact?
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here, and we will get back to you shortly!
Gideon Coleman
I want to explore a few best cybersecurity courses for career growth, but confused about which one is better, I want to consult a Janbask consultant on this.
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here, and we will get back to you shortly!