19
SepGrab Deal : Upto 30% off on live classes + 2 free self-paced courses - SCHEDULE CALL
To properly give a security demonstration that fulfills all the unique and real-life business issues, Salesforce gives an exhaustive and flexible information security model to verify data at very surprising dimensions. Salesforce also gives sharing tools to open up and enable secure access to information supported business needs. In this blog, we shall discuss the Salesforce Security Model. However, the first step towards a successful career as a Salesforce professional is to consider enrolling in a certified and industry-recognized Online Salesforce Training program.
Salesforce limits information presentation to keep up the security on different dimensions. Salesforce makes verification of users to maintain a strategic distance from information access by unapproved users. For user validation, salesforce assembles a mix of verification techniques that are reasonable for hierarchical needs just as the users need. It might incorporate Password, Two-Factor Authentication, Network-based security, Session security, and so forth.
Salesforce possesses the ability to declare different sharing tenets for various dimensions.
Salesforce Training For Administrators & Developers

You can control which users approach which information in your entire organization, a particular article, a particular field, or an individual record.
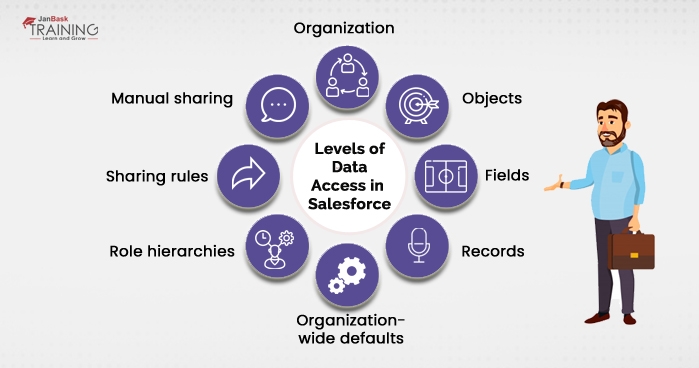
For your entire organization, you can keep up a list of approved users, set password approaches, and limit logins to specific hours and/or areas.
Tip: If you are a beginner in Salesforce, consider going for a Salesforce Cloud Course to move your career on the right path.
Access to object-level information is the most straightforward thing to control. By setting consent on a specific sort of item, you can keep a gathering of users from creating, viewing, altering, or erasing any records of that object. For instance, you can utilize object authorizations to guarantee that interviewers can see positions and employment applications but not alter or erase them.
You can confine access to specific fields, regardless of whether a client approaches the item. For instance, you can make the compensation field in a position object imperceptible to interviewers but visible to procuring supervisors and enrolment specialists.
You can enable specific users to see an item, yet then limit the individual article records that they're permitted to see. For instance, an interviewer can see and alter her own surveys, yet not the audits of different interviewers. You can oversee record-level access in these four different ways.
Are you just starting out in CRM? Here is the Salesforce CRM Tutorial Guide For Beginners!
Indicate the default dimension of access users have to every other's records. You use organization-wide sharing settings to secure your information to the most prohibitive dimension, and afterward utilize the other record-level security and sharing instruments to specifically offer access to different users.
It gives access to users who are higher in the chain of command to all records possessed by users who are underneath them in the organizational order. Job progressive systems don't need to coordinate your association outline precisely. Rather, every job in the progression ought to speak to a dimension of information access that a user or a team of users needs.
Sharing rules are programmed in special cases to association-wide defaults for specific gatherings of users, so they can get to records they don't claim or can't ordinarily observe. Sharing rules, similar to job orders, are just used to give extra users access to records. They can't be stricter than your association-wide default setting.
It enables proprietors of specific records to impart them to different users. Albeit manual sharing isn't mechanized like organization-wide sharing settings, job orders, or sharing tenets, it tends to be helpful in a few circumstances, for example, when an enrolment specialist who is taking some time off has to assign his records to some other person so that the workflow is not disturbed.
Also, here is an Inside-Out Guide on Salesforce, explaining – How Important is to Know About the Map in Salesforce in 2022?
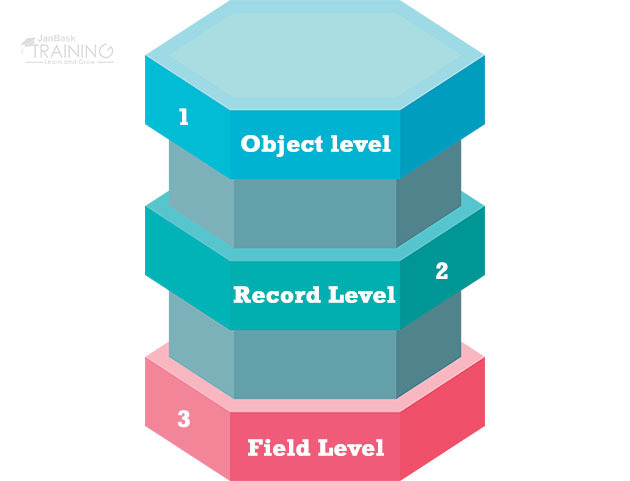
Working up of the Salesforce Data security is separated into layers specifically-
In order to understand this let us assume a specific scenario. Jenny is a working lady. She is an accomplished pioneer who has joined the XYZ association recently. She additionally has extensive experience with marketing and she reports specifically to the CEO of the organization.
In Salesforce, profiles control access to the object level and field-level security among elective things like applications, tabs, etc.
Since Jenny is a new recruit, the partner administrator needs to add Jenny to the worthy profile that has access to the sales applications and related items to begin giving her access to the Salesforce information.
Permission sets in Salesforce Object-Level Security
Since Jenny includes a marketing foundation, suppose she needs to get to the Campaigns object to help with advertising. Be that as it may, since she is as of now an essential constituent of the business profile, on the off chance that an administrator includes CRUD (Create, Read, Update, and Delete) to Campaigns, at that point everybody inside the profile can get to Campaigns. The administrator needs to allow authorization to get to Campaigns just to Jenny. this is the place consent sets come in. Consent sets are utilized to give further (typically unique) authorizations to users who are now in a profile. For our situation, an administrator needs to deliver an authorization set that gives access to the Campaigns object and allocate that consent set to Jenny.
Salesforce Data Security permission
In case, you are preparing to appear for your Salesforce Cloud Consultant certification? We recommend you to go through various Salesforce blogs available on the JanBask Training that has been curated to help you become Salesforce-ready!
Regardless of whether Jenny has the opportunity to get to every one of the things, it's not adequate for her, despite everything she needs access to singular fields of each item. In Salesforce, profiles likewise control field-level access. An administrator will give examine and compose consents to singular fields. an administrator can likewise set a field to cover up, completely concealing the field to that client.
Aside from the access level of the field, Salesforce permits field level security by setting some field properties as given below:
Hopefully, you are clear on how to get the Salesforce Security token. In the next section, you will check how to keep the token secure. Meanwhile, take this free, 2-minute Salesforce quiz to see how much you know about the platform and to keep up with new developments.
Learn Salesforce in the Easiest Way

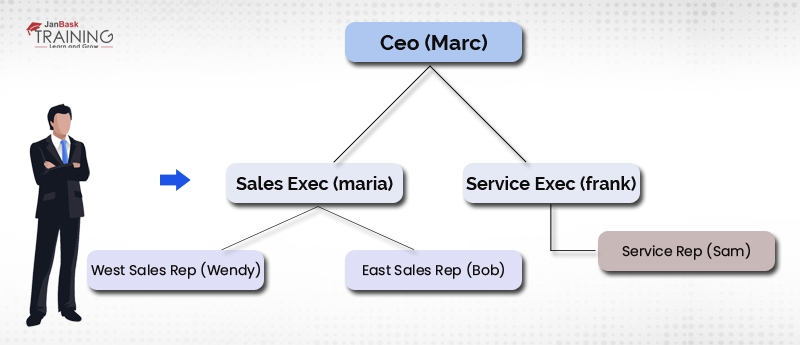
With basically object-level access and field-level access, Jenny can exclusively get to records that she possesses (that is, records made by her). Be that as it may, on the off chance that you take a gander at the association structure, she reports to marc (CEO) and has 2 deals reps (Wendy and Bob) reporting to her.
Salesforce enables you to impart your records to others setting authorizations like Full access, Read/Write, Read just and private access. In Full access client can alter, erase, exchange and view the record. The client can even stretch out sharing access to different users. In reading/Write get to the client can perform just Read or compose activities on record. In reading, just mode client can just view the record. In private mode, the record isn't imparted to some other client.
Salesforce Record Level Data Security
Data Security is an important part of Salesforce learning. to enhance your domain knowledge check out this comprehensive blog on the roles and responsibilities of salesforce developers.
i. Record-level-security: Organization-wide sharing defaults
In Salesforce, records have a field known as "OwnerId" that focuses on a genuine client. proprietors of records are ordinary individuals who made the record and have full CRUD access to it. Salesforce gives elective manners by which to consequently dole out proprietorship to users and to exchange possession from one client to an alternate client
Organization-wide defaults (OWD) control all the conduct of how every single record of a given object (for instance, Accounts) will be accessed by the users who don't claim the record.
For example:
Record-level-security: organization-wide sharing defaults
Collaborate and study with fellow Salesforce professionals, become a part of the JanBask community to build your skills and network, and take your Salesforce career to the next level.
ii. Record-level-security: Role hierarchies
Basically, all organizations have an association structure wherever groups of individuals report back to their administrators and their chiefs thusly answer to their supervisors, shaping a tree-like organization graph. In order to rearrange sharing, Salesforce gives a clear method to impart records to directors. To utilize this sharing guideline, an administrator should initially add the user to a job and allow access.
Securing data is of paramount importance. Salesforce understands this and that is why as already demonstrated above, it provides various ways in which you can keep your data guarded. By understanding the Salesforce Data Security model, you can ensure the greater safety of your data. Don’t wait anymore, jumpstart your Cloud career, and enroll yourself in a comprehensive Online Salesforce Training, today!
Salesforce Training For Administrators & Developers

Q1. Is learning Salesforce challenging?
Ans: Salesforce is easy to learn despite its magnitude. If you thoroughly research the CRM and invest enough time in it, you may master Salesforce within weeks and launch your career with the best Salesforce entry-level employment.
Q2. What is the best thing to learn about Salesforce?
Ans: Most Salesforce experts recommend Trailhead as the greatest resource for getting started with the platform and brushing up on your skills. This is a learning resource that Salesforce has created for its customers. It is comprehensive and factual.
Q3. Which Salesforce certification would you recommend starting with?
Ans: The free Salesforce Admin Trailmix contains all the courses you need to study for your certification exam, and Salesforce Trailhead is a wonderful place to get started.
Q4. How long does it take to become a certified Salesforce Developer?
Ans: It would take the applicant three to four months to study Salesforce admin skills, more than five months to get ready for Salesforce development skills, and roughly six months to learn.
Q5. What skills are necessary for a Salesforce professional?
Ans: The following are the top skills a Salesforce professional should possess:
Q6. How can someone without experience find work in Salesforce?
Ans: However, prior work experience is not required to start a career with Salesforce. You ought to understand the fundamental ideas behind Java and Salesforce (OR).
Q7. How challenging is it to land a position at Salesforce?
Ans: As one of the most reputable corporations in the world, Salesforce has a tough hiring process. According to online employee reviews, "internal referrals" appear to be a recurrent trend when it comes to filling available positions at this company.
Q8. What qualification is required for Salesforce professionals?
Ans: The ideal candidate should be an administrative professional with a BE-A degree and a background in Salesforce. They should also have a BBA, BCA, or MCA. Developers, Administrators, authors, journalists, and analysts can all benefit from the internationally recognized Admin certification.
Q9. What are the top programs that integrate with Salesforce?
Ans: The major programs that interact with the Salesforce platform are listed below –
Q10. What is the best way to prepare for the Salesforce interview?
Ans: You can begin your preparation with :
I am a seasoned IT professional with a total experience of 8 years. During my course of work, I have been engaged in several projects. I have hands-on experience in leading CRM systems like Salesforce and Pega. I am currently employed as a Test Lead and is enthusiastic to learn and explore new technologies.

Cyber Security

QA

Salesforce

Business Analyst

MS SQL Server

Data Science

DevOps

Hadoop

Python

Artificial Intelligence

Machine Learning

Tableau
Interviews