 Grab Deal : Flat 30% off on live classes + 2 free self-paced courses! - SCHEDULE CALL
Grab Deal : Flat 30% off on live classes + 2 free self-paced courses! - SCHEDULE CALL

 Grab Deal : Flat 30% off on live classes + 2 free self-paced courses! - SCHEDULE CALL
Grab Deal : Flat 30% off on live classes + 2 free self-paced courses! - SCHEDULE CALL

Life has become more and more comfortable with the spread of various digital devices and the Internet. All good things have a downside, and that's true in today's digital world as well. The Internet has brought about positive changes in our lives today, but it also poses great challenges in protecting data. This leads to cyber attacks. Therefore, having a strong foundation in cyber security field is very important. You can learn about plethora of cybersecurity concepts by enrolling in top cybersecurity courses. Let’s discusses about different types of cyberattacks and how to prevent them. To learn more about the cybersecurity training we offer, please visit our training page.
Cyber security also referred as information technology security is a technique to protect and safeguard internet connected cyber space i.e., systems, networks, devices, programs and data from unauthorized access.
Any unlawful and malicious attack by an individual or organization to damage or steal or disrupt a digital system is a Cyber security threat also known as Information security threat.Information threats can emerge from various actors such as corporate spies, hacktivists, terrorist groups, hostile nation-states, criminal organizations, lone hackers and disgruntled employees.As cybersecurity threats continue to evolve and become more sophisticated, enterprises must think of the types of security threats they are dealing with.
Below is a detailed explanation of each type of cyber security threats:
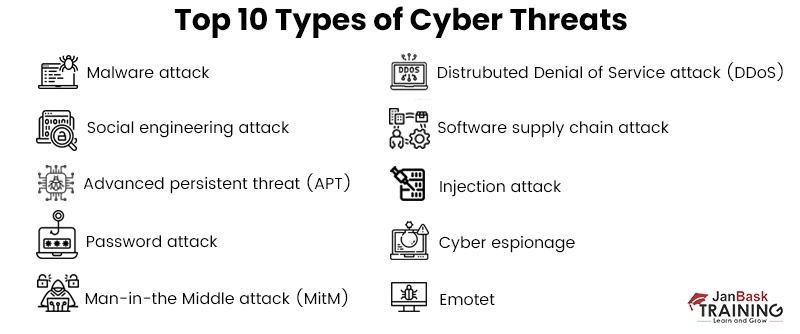
Malware is a malicious software which is activated when a user clicks on a malicious link or attachment leading to installing dangerous software.
Once installed, malware can monitor user activities, share confidential data to the attacker, assist the attacker in penetrating other targets within the network, and even cause the user’s device to participate in a botnet leveraged by the attacker for malicious intent.
Wiper Malware - It is a type of malware which tends to threaten the system by overwriting the files or completely crashing an entire device through manipulation. Such software is generally designed to send and create communal disturbance through politically sensitive messages, organizations crucial, valuable documents and country’s secret assets.
Worms – A malware that can self-replicate without any human interaction. A threat actor can spread the malware across the network through this technique.
Spyware – It is a type of obnoxious software which helps malicious actors to gather unauthorized data including company patent formula, Individual payment details and personal data. Spyware largely affects mobile phones, desktop applications, web browsers etc.
Trojan virus – Trojan is a malicious software which pretends to be legal and normal as other software but hides through apps, browser extensions, games or email attachments. Downloading such a virus unknowingly leads to further devastation and complete breaking down of the device.
Ransomware – An organization or individual is being denied access to its own networking system or data via encryption and in exchange demands a Ransom to be paid to restore access of assets. There is no complete guarantee that the owner would be able to restore his/her whole data after successful payment.
Fileless Malware – This type of threatening software does not require installation or download, instead get access to the intended system through native files like Power shell and WMI being editable and represented as legitimate and undetectable.
Rootkits – Rootkits are super imposable software which are injected to a targeted or intended networking application, operating system kernels or hypervisors leading to give key and ultimate administrative control of the entire system. In such cases an attacker or hacker can operate in a congested environment to make him/her unrecognizable or unidentified.
Socially induced attacks are mainly where the user is psychologically manipulated according to the attacker's desire and intention so as to get consent to misuse one’s information.
It generally contains the followings such as:
Honey Trap- In such circumstances social workers create fake identity and accounts to attract a target user online. Through continued online relationships, social attackers try to get important and sensitive information.
Pharming- It is an online fraud scheme through which a hacker consciously installs malicious code and software directing users automatically to unwanted and fake websites enabling them to provide personal data.
Scareware Security Software- Such software pretends to be a security scan for malware but regularly shows unprecedented warning and detections. Cyber criminals may ask to pay in order to remove warnings which ultimately lead to being shown off the user financial details.
Phishing- In such attacks criminals may share fake codes that seem to come from legitimate and legal sources such as email, browser extensions etc which directs one to perform certain actions such as accepting cookies, accepting terms and conditions which may lead to exposing sensitive information.
Vishing- Through vishing or voice phishing numerous attackers may access one’s financial information details through mobile phone.
Spear phishing- Phishing which majorly targets security privileged or influential persons to leak crucial and private data.
Whaling- It is a category of phishing where an attacker only targets highly influenced and responsible personnel like Attorney General, Financial advisory secretary, Chief Executive Officers (CEO) etc to enable the intended information.
Drive by Downloads- Malware gets automatically installed or downloaded to a user's system without his consent when exploring unauthorized advertisements or websites through HTTP or PHP on a page. Users are directed to click certain actions by hackers which helps to provide valuable information unlawfully.
APT is a laborious and sophisticated type of threat where a criminal or group of criminals when they get unauthorized access to a certain platform and become undetectable for a longer period of time against organization’s security radar then try to succumb to a large amount of crucial data. As it demands huge effort and mind set hence mainly done against major religious as well as corporal institutions, nation-state etc.
Major indicators highlighting the presence of APT are
In certain cyber threats, attackers gain unlawful data and information from targeted individual’s operating systems through guessing the password, social engineering or systematic breach to passwords.
Password attack may contain the followings
Brute-force – Hackers in order to get access to data use different software with various passwords by guessing to get a corrected one. Software involves a certain analogy to get a password related to the name of a person and any of his relatives etc.
Dictionary Attack - Certain sets of dictionary common passwords are used in the hope to get a corrected one for target operation.
Pass-the-Hash Attack – Criminal exploits the authenticated passwords and gets a password hash and uses it for authentication of another operating system.
Golden Ticket Attack – Following the same way in the previous attack, a hacker uses the assessed stolen password hash on a Kerberos system to enable the key Distribution center to leak a Ticket Granting Tickets hash. (TGT)
In MitM, a cyber-criminal is assumed to be a middle man between the user and the target system.
Once a middleman is well established, it may steal important information and data, misusing responses and responsibilities and even tries to compromise the user's credentials.
MitM includes following categories of middle man hacking
It is an active variant of DoS where an attacker uses multiple systems in the form of coordinated attack against a particular target system. In such a type of security threat, the users’ resources get overwritten and stop functioning leading to further denial of functions.
As such a threat is created in a combined and compromised form hence easily being undetected against High security systems.
Botnets - Botnets are infected applications with malwares under the control of an attacker. Criminals use similar bots for attacking other targets creating a huge devastation of information.
Smurf Attack - It sends Internet Control Message Protocol (ICMP) echo requests to the user’s IP address which automatically get attached to the victim’s device and infiltrate desired target data.
TCP SYN Flood Attack - In such a type of attack, the attacker sends floods of continuous connection requests with the target system, if the target tries to complete the connection, then the attacker doesn't respond resulting in the user's time out. It immediately fills the connection queue, preventing legal users from connecting with the system
HTTP Flood Attack - Hacker sends HTTP request to user’s system which seems to be legitimate to overwhelm its web server. Such an attack forces the target device to allocate as many as resources to get requisite information.
UDP Flood Attack - In such an attack key host or primary device is flooded with User Datagram Protocol packets which are sent to random ports. UDP further forces cyber victims to search in the affected port and reverse response with “Destination unreachable”.
NTP Amplification Attack - The attacker exploits publicly accessible Network Time Protocol (NTP) servers to overwhelm the target with User Datagram Protocol (UDP) traffic.
It is a type of security attack mainly designed against major organizations intending to target weak and pirated links in its trusted supply chains and software updates. As the supply chain is interwoven with resources, multiple operations, multiple mini networks hence crashing and stealing any segment of the software device may lead to avail unauthenticated data access.
Supply chain attack majorly affects the trusted organizations of the main organization such as third-party vendors and supporting ecosystems.
Types of software supply chain attacks:
To steal information through injecting and inserting certain malicious code or applications. It may lead to compromise of the entire system, expose public information and even execute a DoS attack.
Injection may be of following types
Cyber espionage or Cyber spying is a kind of cyber threat where a malevolent user tries to get highly classified or sensitive data, Intellectual property for financial advantage, competitive gain, political or religious manifestation.
Cyber spies Majorly attempt to access the following properties:

Cyber Security Training
“Emotet is an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. It continues to be among the most costly and destructive malware.” – as described by The Cybersecurity and Infrastructure Security Agency (CISA)
You’ve understood everything about CyberSecurity attacks through this blog.
What is ethical hacking and types of ethical hacking.
Training for cybersecurity students is now offered in the form of fundamental and advanced level cybersecurity Courses. This has become the only way to better educate students because of the recent rapid developments in the field of technology and the fact that cybercriminals are constantly learning new tricks to defraud people.

What are Attack Vectors in Cyber Security?

Information Warfare: War In The 21st Century

Cyber Security

QA

Salesforce

Business Analyst

MS SQL Server

Data Science

DevOps

Hadoop

Python

Artificial Intelligence

Machine Learning

Tableau
Download Syllabus
Get Complete Course Syllabus
Enroll For Demo Class
It will take less than a minute
Tutorials
Interviews
You must be logged in to post a comment