Introduction
 Businesses that need more safeguards in place risk sailing in waters where cybercriminals thrive in today's rapidly changing cyber security scenario. Every company must develop preventative best practices to deal with constantly changing threats and significant data breaches and should be thinking about how to learn cyber security to avoid all types of cyber attacks.
Businesses that need more safeguards in place risk sailing in waters where cybercriminals thrive in today's rapidly changing cyber security scenario. Every company must develop preventative best practices to deal with constantly changing threats and significant data breaches and should be thinking about how to learn cyber security to avoid all types of cyber attacks.
Wondering how to learn cyber security? The cyber security landscape is continuously evolving, and companies implementing enough security are sailing in the water where cybercriminals are thriving. With the ever-evolving threats and significant data breaches, companies should follow the best preventive practices to ensure consistent growth. The best way to learn cyber security is to join Online Cyber Security Courses to gain in-depth cybersecurity knowledge. These are suitable for cybersecurity for beginners and professionals.
As reported by the Juniper Research prediction, between 2017 and 2022, cyberattacks will cost international corporations $8 trillion overall. In the same time frame, it is predicted that the cost of cyberattacks will climb by 30% while spending on cybersecurity will only rise by 8%.
There have been many different security issues since the digital concept was introduced. Their severity can range from a slight annoyance to devastating, and you can be sure various malicious types of cyber attacks will remain as long as the digital world does. However, despite how scary it may sound, several prevalent security dangers are several overall security dangers that can be recognized and avoided. This blog will discuss the top types of cyber attacks people face and the right solutions to prevent them. Before we move to the different types of cyber attacks, let’s first go through the cyber security basic and types of cyber attacks.
Stay tuned!
A Quick Overview on Cyber Attack
A cyberattack is an attempt to acquire unauthorized access to an IT system by an attacker for theft, extortion, disruption, or other evil motives.
In other words, when a third party gains unauthorized access to a system or network, the situation is a cybersecurity attack. A hacker or attacker is someone who conducts a cyberattack.
Cyberattacks have several negative results. When an attack is conducted, it may result in data breaches, which may cause data loss or manipulation. Companies suffer financial losses, reduced customer trust, and reputational harm. We employ cybersecurity to prevent cyberattacks. Network, computer, and their component protection from unwanted digital access is known as cybersecurity. Understanding Cyber Security is essential to stop the spread of cyber attacks, and the best way to learn cyber security is through cyber security courses.
Cyber Security Training & Certification
- Detailed Coverage
- Best-in-class Content
- Prepared by Industry leaders
- Latest Technology Covered
How do Cyber Attacks Happen?

When a person, group, or organized group tries to infiltrate the security system of another person or organization maliciously, that attempt is known as a cyber attack. The most common example of a cyber attack is a data breach. It happens when hackers get past a company's or organization's security and take sensitive data. They sell it on the Dark Web, use it for various types of fraud, or use it as information for extortion.
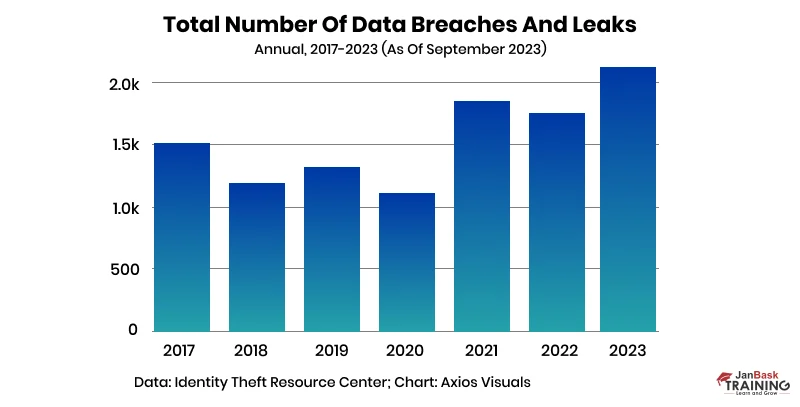
The total number of data breaches and leaks in 2023 so far has already outpaced last year's numbers, according to new data from the Identity Theft Resource Center. Through September, the ITRC tracked 2,116 data compromises — a 17% increase from the 1,802 total compromises tabulated in 2022. After these numbers, you are wondering how to learn cyber security.
Data leak is just one of the effects of cyberattacks, though. Cyber attacks also focus on stealing identity by obtaining personal information, or malicious groups can employ them to damage an organization's networks.
On average, data breaches typically cost businesses over $4 million. If a hacker gains access to an individual's internet accounts and sensitive data, such as Social Security numbers and birthdays, they could lose everything. While you are clear with the cyber security basics, consider joining the JanBask Training Cyber Security Community for the proper guide to cyber security and expert advice.
Sources of Cyber Threats
Identifying the source of cyber threats is crucial to understanding where they come from, who has done this, and why. Some of the familiar sources of cyber threats include:
- State-sponsored
- Terrorists
- Industrial spies
- Organized crime groups
- Hackers
- Hacktivists
- Malicious insider
- Cyber espionage
Now that you are clear on a cyber attack, let's check through different types of cyber attacks.
56 Types of Cyber Attacks You Should Be Aware of in 2025
There are various types of cyber attacks; we have listed here top 13 that you should be aware of -:
1. Phishing Attack
One of the most significant types of cyber attacks, a Phishing attack is a type of social engineering attack wherein the attacker presents himself as a trusted contact and sends the victim fake emails.
The unaware victim opens the mail and clicks on the malicious link. Once the user clicks on the send link, the attackers gain access to confidential information and account credentials.
Following are the quick ways to prevent these phishing attacks –
- Always scrutinize your received mail ‘
- Take advantage of an anti-phishing toolbar
- Keep your password updated.
2. Malware
Malware is an application that can carry out several dangerous functions in cybersecurity. Malware strains are made to spy on users to gather credentials or other significant information to create persistent access to a network. Some malware is created to disrupt normal operations. Malware can sometimes be explicitly created to extort the victim. Ransomware is among the well-known types of cyber attacks. Malware is created to encrypt the victim's files and demand payment in exchange for the decryption key. Preventing malware is a challenging task that necessitates a multifaceted strategy.
The following are the key strategies to prevent malware –
- Ensure that you have installed the most up-to-date anti-malware and spam protection software. Ensure that everyone on your team is trained to discover phishing emails and websites.
- Have a robust password policy and implement multifactor authentication.
- Update and patch all of your software. Use the Administrator accounts under dire circumstances only
- Control system and data access carefully.
3. SQL Injection Attack
When a user modifies a typical SQL query on a database-driven website with wrong intentions, it results in a Structured Query Language (SQL) injection attack. It is spread by inserting malicious code into a vulnerable website search box and forcing the server to divulge essential data.
After this cyber security network attack, the hacker gets access to read, edit, and remove databases' tables and administrative rights.
Following are the ways to prevent SQL injection attacks –
- Do proper validation of the user-supplied data.
- Use an Intrusion detection system as they design it to identify unauthorized access to a network
4. A Denial-of-Service Attack
A Denial-of-Service Attack poses a severe risk to businesses. Attackers target systems, servers, or networks, in this case, and bombard them with traffic to deplete their bandwidth and resources.
When this occurs, the servers get overburdened with serving incoming requests, which causes the website it hosts to either go down or slow down. The valid service requests go unattended as a result. When attackers employ numerous hacked systems to initiate this attack, it is sometimes referred to as a DDoS (Distributed Denial-of-Service) attack.
Following are the ways to prevent DDoS attacks –
- Do a traffic analysis to find malicious traffic
- Get a proper understanding of the warning signs like network slowdown, intermittent site shutdowns, etc.
- Create a response plan, get a checklist and ensure your team can handle a DDoS attack
5. Cryptojacking
Cryptojacking is one of the cyber attacks under which cybercriminals steal a user's computer or other device and use it to mine cryptocurrencies like Bitcoin. Although cryptojacking is not as popular as other cybersecurity attacks, it shouldn't be discounted. When it comes to this kind of assault, organizations don't have great visibility, thus, a hacker can use priceless network resources to mine a cryptocurrency without the organization being aware of it.
Following are a few techniques to prevent cryptojacking –
- Monitor the CPU consumption of all network devices, including any cloud-based infrastructure you use
- Inform your team to stay alert for any performance difficulties or suspicious communications that might be infected with Cryptojacking viruses
6. Insider Threat
An insider threat, as the name implies, involves an insider instead of a third party. The attacker can be someone who works for the company and is well-versed in its operations. The potential damage from insider threats is enormous. Small organizations are particularly vulnerable to insider threats because their employees hold access to sensitive data. There can be numerous reasons for this attack, including avarice, malice, and even negligence. Insider threats are tricky because they are difficult to predict.
These are some of the most effective ways to prevent this cyber attack –
- Create a strong culture of security awareness within your organizations
- Depending on their employment functions, companies must restrict the IT resources employees can access.
- Organizations should educate the team on how to recognize insider threats. It will help them to recognize when a hacker attempts to misuse data from the firm.
Check out our guide on how to become a cyber security expert and give an edge to your career graph.
7. Password Attack
Password Attack, as the name suggests, is one type of network attack in which the attacker tries to “crack” a user's password. It is possible to find a user's password by using different methods, albeit it is outside the scope of this article to explain each process in detail. Besides, hackers try to attempt by using phishing techniques to access a user's password.
Following are a few ways to prevent these types of cyber attacks –
- Make your passwords strong by using alphanumeric and special characters
- Do not use the same password across several accounts or websites.
- Keep updating your passwords to reduce the risk of a password attack.
- Keep any password suggestions hidden from view.
8. Man-in-the-middle Attacks
One of the unique types of cyber attacks, the man-in-the-middle (MITM) assault, occurs when hackers interject themselves into a two-party transaction. According to Cisco, they can filter and take data after disrupting the traffic. These types of cyber attacks are more frequent while using public Wi-Fi networks because they are so simple to exploit. Attackers place themselves in the way of the visitor and the network, then use malware to set up malicious software and access data. For example, hackers interject themselves into your dialogue and pose as the other party you believe you are speaking to.
Some of the effective ways to tackle these kinds of cybersecurity attacks are mentioned below–
- Your first line of security should be a secure internet connection
- Focus on using a VPN (virtual private network) when connecting online
- There should be endpoint security, and multi-factor authentication
Before we move further, let’s go through the quick guide on how to boost Cybersecurity salary for freshers and experienced!
9. DNS Tunnelling
Hackers use DNS tunneling, one of the types of network attacks, to get around more established security measures like firewalls and access systems and networks. Hackers code malicious programs with DNS requests and responses. Once inside, the malware latches onto the target server and grants the attackers remote access. These types of cyber attacks are harmful mainly because they sometimes go unreported for days, weeks, or months. Cybercriminals can install malware, modify code, add new access points, and steal critical data during that period.
These are the ways to prevent DNS Tunneling attacks –
- Deploy an effective DNS filtering system
- Train your team to recognize atypical DNS traffic patterns.
- Invest in a proper DNS-specific firewall
10. Cross-site Scripting Attacks
Under cross-site scripting (XSS) cyber-attacks, hackers access a website or application without any authority. They try to take advantage of weak websites and force malicious JavaScript installations on visitors. After the building, the hacker can access your account and do whatever action when the code is executed in your browser. Web pages, forums, and message boards are examples of vulnerable sites to XSS. These web pages depend on user input that has not been checked for harmful code. However, even more, prominent locations are vulnerable. You can explore more about Cyber Security through insightful articles and training courses at JanBask Training!
Here are some effective techniques of preventing this cybersecurity network attack –
- Make sure your applications validate all the input data
- Only listed data should be allowed in the system
- Also, make sure that all variable output in a page is encoded before it is returned to the user
11. Botnet Attack
This kind of attack generally targets large-scale corporations and associations because of its extensive information access. Under it, the attackers can take over many devices and bargain them into serving their cunning purposes. Owners of botnets can command a few thousand PCs to perform malicious actions by approaching them all at once. Cybercriminals initially gain access to these devices by using specialized Trojan infections to compromise the security frameworks of the PCs. They order and control software to enable them to perform malicious actions with a broad audience. These drills can be mechanized to enable as many synchronized types of cyber attacks as possible.
Here are some ways to prevent this cyber attack –
- Control access to machines and systems
- Run regular antivirus scans
- Deploy multi-factor authentication
12. Spear-phishing Attacks
A specific kind of targeted phishing attack is spear phishing. The attacker spends time learning about their chosen victims before crafting communications that are likely to be of personal interest to them. Due to the manner, in which the attacker focuses on a single target, these types of cyber attacks are fittingly referred to as "spear" phishing. Because the message will appear authentic, it may be challenging to recognize a spear-phishing attempt.
A spear-phishing assault frequently uses email spoofing, in which the "From" line of the email is altered to make it appear as though a different sender is sending it. This might be a friend, business partner, or someone the target trusts from their social network.
Effective ways to prevent phishing attacks --
- Carefully check out the details in all fields of an email
- Make sure not to click on any link whose destination cannot be verified as legitimate.
13. URL Interpretation
By manipulating and fabricating specific URL addresses, attackers can exploit URL interpretation to access the target's personal and professional data. The term "URL poisoning" is another name for this type of attack. The term "URL interpretation" refers to the attacker knowing the correct order in which to enter the URL components for a web page. The attacker then "interprets" this syntax, utilizing it to determine how to get access to restricted locations.
A hacker may guess URLs they can use to get administrator access to a website or access the site's back end to enter a user's account to carry out a URL interpretation attack.
These are a few ways to prevent this cyber attack-
- Use secure authentication methods for any sensitive areas of your site
- Ensure multi-factor authentication (MFA) or secure passwords
14. Zero-Day Exploit
A Zero-Day Exploit happens after the announcement of a network vulnerability; there is no solution in most cases. Hence, the vendor notifies the vulnerability so that the users are aware; however, this news also reaches the attackers.
Depending on the vulnerability, the vendor or the developer could take time to fix the issue. Meanwhile, the attackers target the disclosed vulnerability. They make sure to exploit the vulnerability even before a patch or solution is implemented for it.
Zero-day exploits can be prevented by:
- Organizations should have well-communicated patch management processes. Use management solutions to automate the procedures. Thus, it avoids delays in deployment.
- Have an incident response plan to help you deal with a cyberattack. Keep a strategy focusing on zero-day attacks. By doing so, the damage can be reduced or completely avoided.
15. Water Hole Attack
Generally used to target organizations, water hole attacks occur when a group infects websites a particular organization frequently uses. Much like a cross-site attack, the goal is to load a malicious payload from the infected sites.
Prevention: Anti-virus can passively identify dangerous scripts. Keep website scripts off as a default if your enterprise suspects an infection.
16. Spoofing
An attacker impersonates someone or something else to access sensitive information and do malicious activities. For example, they can spoof an email address or a network address.
Prevention: One effective way to prevent spoofing types of cyber attacks is to enable spam filters in your email.
17. Identity-Based Attacks
These types of cyber attacks are performed to steal or manipulate others' personal information, like logging someone's PINs to steal unauthorized access to their systems.
Prevention-
- Deploy risk-based access management.
- Identify Identity-specific triggers for response.
- Ensure Identity visibility across the technology.
18. Supply Chain Attacks
Exploit software or hardware supply chain vulnerabilities to collect sensitive information.
Prevention-
- Identify cyber risk during the onboarding phase
- Scale vendor risk management with automation
- Continuously monitor supply chain risks
19. DNS Spoofing
This is one of the types of cyber attacks where an attacker manipulates the DNS records from a website to control its traffic.
Prevention: To protect from DNS spoofing, internet providers can use DNSSEC (DNS security). When a domain owner sets up DNS entries, DNSSEC adds a cryptographic signature to the entries required by resolvers before they accept DNS lookups as authentic.
20. IoT-Based Attacks
IT teams that exclusively focus on identifying external adversaries are only obtaining a partial understanding of the overall threat landscape. Insider threats, which consist of current or former employees, present a significant danger to organizations due to their unrestricted access to the company network, including sensitive data and intellectual property. Their familiarity with business procedures, company policies, and other relevant information can aid in carrying out an attack.
Prevention: IoT devices are typically interconnected, which means that if one device is compromised, the attack may spread to other devices. To make matters worse, IoT devices hardly have any built-in security, which makes them a perfect target for adversaries. In addition to implementing general security measures, you will need to ensure that you change the default router settings, use a strong and unique password, disconnect IoT devices when they are not in use, and ensure they have the latest patches/updates installed.
21. Ransomware
A malware variant, ransomware, installs itself on a user's system or network. Once installed, it prevents access to functionalities (in part or whole) until a “ransom” is paid to third parties.
Prevention: Removal is challenging once installed. Keeping anti-virus updated and avoiding malicious links are the best current prevention methods. Also, current backups and replications are vital to keeping ransomware attacks from becoming catastrophic. There are various cybersecurity guides and books available that can enhance your knowledge.
22. Distributed Denial of Service (DDos) Attacks
Flood a website with traffic to make it unavailable to legitimate users and to exploit vulnerabilities in the specific network.
Prevention: Several methods for reducing this exposure include restricting traffic to specific locations, implementing a load balancer, and blocking communication from outdated or unused ports, protocols, and applications.
23. Spamming
Spamming is the use of messaging systems to send multiple unsolicited messages to large numbers of recipients for the purpose of commercial advertising, non-commercial proselytizing, any prohibited purpose, or simply repeatedly sending the same message to the same user.
Prevention:
- Be careful about releasing your email address.
- Check privacy policies.
- Be aware of options selected by default.
- Report messages as spam.
- Don't follow links in spam messages.
- Disable the automatic downloading of graphics in HTML mail.
24. Automated Teller Machine (ATM) Cash Out
Hackers get close to a bank's computer systems to withdraw large amounts of cash from ATMs. These types of cyber attacks have become quite popular and common today.
Prevention:
- Check the machine for any attached foreign or unrecognized devices.
- Refrain from entering ATMs in desolated areas or without a guard.
- Check for any hidden cameras.
- Leave the premises if you see suspicious people lingering inside or around the ATM
25. Whale-Phishing Attacks
These types of cyber attacks happen by target high-profile individuals like executives or celebrities using sophisticated social engineering techniques to get sensitive information.
Prevention: Remaining skeptical of suspicious messages, friend requests, emails, or attempts to collect user info from unknown third-parties.
26. Spear-Phishing Attacks
Target specific individuals or groups under an organization. Attackers use social engineering techniques to get sensitive information.
Prevention: Filter Your Email and Implement Anti-Phishing Protection
27. Session Hijacking
The hacker gets access to a user's session ID to authenticate the user's session with a web application and take control of the user's session.
Prevention: Use strong passwords and multifactor authentication.
28. Brute Force Attack
An attacker gets unauthorized access to a system by trying various passwords until the correct one is found. It can be highly effective against weak passwords.
Prevention: Restricting IP access is probably the most robust measure that you can take to protect your sensitive login and admin pages from brute force attacks. Any requests not originating from an approved IP address will result in a 403 Forbidden response error or firewall block page.
29. Web Attacks
This is one the types of cyber attacks that target websites and can insert SQL injection, cross-site scripting (XSS), and file inclusion.
Prevention: install a personal firewall along with anti-malware tools with the latest malware definition file updated that can detect malware such as keyloggers; 3. employ different sets of login and password combinations for different web applications and services you use.
30. Trojan Virus
Trojan malware attempts to deliver its payload by disguising itself as legitimate software. One technique used was an “alert” that a user’s system was compromised by malware, recommending a scan whereby the scan delivered the malware.
Prevention: Avoid downloading programs or executables from unrecognized vendors or those that attempt to alarm the user to a serious problem.
31. Drive-by Attacks
In a drive-by-attack, malicious code is delivered onto a system or device. The distinction, however, is that no action is needed on the user end, where typically, they need to click a link or download an executable.
Prevention: Avoid suspicious websites. Normally, compromised websites are flagged by search engines and anti-malware programs.
32. Advanced Persistent Threat (APT)
Is a cyberattack characterized by long-term, persistent access to a victim's computer system. APT attacks are highly sophisticated and difficult to detect and remove.
Prevention-
- Install a Firewall
- Enable a Web Application Firewall
- Install an Antivirus
- Implement Intrusion Prevention Systems
- Create a Sandboxing Environment
- Install a VPN
- Enable Email Protection
33. Angler Phishing Attacks
Target individuals or organizations using highly targeted and personalized emails. Angler phishing attacks can be difficult to detect and are often successful in stealing sensitive information.
Prevention: Education and awareness are crucial in preventing angler phishing attacks. Regularly train employees to identify and report suspicious emails, websites, or phone calls. Encourage them to verify the legitimacy of requests for sensitive information before providing any data.
34. Fileless Malware
Doesn’t rely on files to infect a victim's computer system. Instead, fileless malware executes malicious code using existing system resources, such as memory or registry keys.
Prevention: Update and patch software and systems regularly – Minimize malware entry points through regular updates, as these attacks frequently exploit unpatched vulnerabilities.
35. Emotet
Is malware designed to steal sensitive information and spread it to other computers on a network. Emotet is often spread through phishing emails and can be very difficult to detect and remove.
Prevention:
- Keep your computer/endpoints up-to-date with the latest patches for Microsoft Windows.
- Don’t download suspicious attachments or click a shady-looking link.
- Educate yourself and your users on creating a strong password.
36. Adware
Is malware that displays unwanted advertisements on a victim's computer system. Adware can be annoying and disruptive, but it's generally less harmful than other types of malware.
Prevention:
- Use antivirus software.
- Perform updates.
- Only download apps from known app stores.
- Don't click on pop-up ads.
- Beware of phishing.
37. Keylogger
Is a malware designed to capture keystrokes a victim enters on their computer system. This can include passwords, credit card numbers, and other sensitive data.
Prevention- Software that's outdated or known to be buggy is far easier to exploit. Installing software updates as they become available can help reduce or eliminate the weak points that keyloggers may target. Equip your desktops, laptops, smartphones, and other digital devices with an antivirus firewall.
38. Botnets
Are networks of compromised computers controlled by a single attacker. Botnets can launch distributed denial of service (DDoS) attacks, steal sensitive information, or perform other malicious activities.
Prevention:
- Keep Software and Operating Systems Up to Date: Vendors often release patches for vulnerabilities botnets can exploit.
- Use Antivirus Software: Antivirus software can detect and remove malware that is used to create botnets.
39. Rootkits
Provide attackers privileged access to a victim's computer system. Rootkits can be used to hide other types of malware, such as spyware or keyloggers, and can be challenging to detect and remove.
Prevention: Some basic precautions in avoiding rootkit attacks include Using reputable anti-malware solutions, which will fight against most application-level malware. Keeping software regularly updated, and downloading software only from trusted sources.
40. Spyware
Is malware designed to collect sensitive information from a victim's computer system. This can include passwords, credit card numbers, and other sensitive data.
Prevention:
- Be cautious about consenting to cookies.
- Install an anti-tracking browser extension.
- Keep all software updated with the latest security.
- Remember that “free” software always has a cost.
41. Social Engineering
Social Engineering is a technique cybercriminals use to manipulate users to make them divulge sensitive information or perform actions that are not in their best interest.
Prevention: Keep software and firmware regularly updated particularly security patches. Don't run your phone rooted or your network or PC in administrator mode. Even if a social engineering attack gets your user password for your 'user' account, it won't let them reconfigure your system or install software.
42. Keylogger
Is a malware designed to capture keystrokes a victim enters on their computer system. This can include passwords, credit card numbers, and other sensitive data.
Prevention: Software that's outdated or known to be buggy is far easier to exploit. Installing software updates as they become available can help reduce the or eliminate the weak points that keyloggers may target. Equip your desktops, laptops, smartphones, and other digital devices with an antivirus firewall.
43. Bots
These software programs automate network or internet tasks. They can be used for malicious purposes, such as Distributed Denial of Service (DDoS) attacks.
Prevention:
- Implementing CAPTCHAs and Challenges.
- Advanced CAPTCHA Challenges.
- Rate Limiting and Throttling Requests.
- Employing Web Application Firewalls (WAF)
44. Business Email Compromise (BEC)
A BEC attack is where the attacker targets specific individuals, usually an employee who can authorize financial transactions, to trick them into transferring money into an account controlled by the attacker. BEC attacks usually involve planning and research in order to be effective. For example, any information about the target organization’s executives, employees, customers, business partners, and potential business partners will help the attacker convince the employee to hand over the funds. BEC attacks are one of the most financially damaging types of cyber attacks.
Prevention:
As with other types of cyber attacks, security awareness training is the best way to prevent BEC. Employees must be trained to look out for emails with a fake domain, or emails that impersonate a vendor, display a sense of urgency, and anything else that looks suspicious.
45. Cross-Site Scripting (XSS) Attacks
These types of cyber attacks happen when they target web applications by injecting malicious code into a vulnerable website to steal sensitive information or perform unauthorized types of cyber attacks.
Prevention: To prevent XSS attacks, your application must validate all the input data, make sure that only the allowed listed data is allowed, and ensure that all variable output in a page is encoded before it is returned to the user.
46. AI-Powered Attacks
Use artificial intelligence and machine learning to bypass traditional security measures.
Prevention:
- Never share sensitive info with an unverified contact.
- Check the URL of each landing page when banking online or using another platform to share sensitive information.
- Use strong, unique passwords across all of your accounts.
- Keep your device's security on its strongest setting
47. Dictionary Attacks
An attacker attempts to guess a user's password by trying a list of common words. This attack becomes successful because many users use weak or easy passwords.
Prevention:
- Use Strong and Complex Passwords.
- Use Password Managers.
- Use Two-Factor Authentication.
- Regularly Change Passwords.
- Monitor for Suspicious Activity.
- Slow Down Repeat Logins.
- Use CAPTCHA For Your Organisation.
48. Virus
Malicious software can replicate itself and spread to other computers. Viruses can cause significant damage to systems, corrupt files, steal information, and more.
Prevention: Avoid websites you don't trust. Don't open email attachments from people or companies you don't know. Don't click on links in unwanted emails. Always hover the mouse over a link (especially a short URL) before clicking on it to see where it will take you.
49. Worm
A computer worm is a standalone malware program that replicates itself to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers.
Prevention: install or enable a firewall - Firewalls may prevent some types of infection by blocking malicious traffic before it can enter your computer (see Understanding Firewalls for more information). Some operating systems include a firewall, but you must ensure it is enabled.
50. Backdoors
A backdoor is a typically covert method of bypassing standard authentication or encryption in a computer, product, embedded device, or embodiment. Backdoors are often used for securing remote access to a computer or obtaining access to plaintext in cryptosystems.
Prevention:
- Regularly update your software and security patches. Hackers often exploit vulnerabilities in outdated software to gain access to a system.
- Use strong, unique passwords and enable two-factor authentication to help prevent unauthorized access to your systems and data.
51. Volume-Based Attack
The attacker floods a system with heavy data to make it inaccessible to legitimate users. For instance, DDoS attacks in which various compromised computers flood a specific website with traffic to crash it.
Prevention: You can use firewalls or Access Control Lists (ACLs) to control what traffic reaches your applications. The two key considerations for mitigating large-scale volumetric DDoS attacks are bandwidth (or transit) capacity and server capacity to absorb and mitigate types of cyber attacks.
52. Protocol Attacks
Exploits vulnerabilities in network protocols to gain unauthorized access to a system or disrupt its regular operation. Examples include the Transmission Control Protocol (TCP) SYN Flood attack and the Internet Control Message Protocol (ICMP) Flood attack.
Prevention: Create blockhole routing, rate limiting, and use a web firewall.
53. Application Layer Attacks
This is one of the types of cyber attacks that target the application layer of a system, aiming to exploit vulnerabilities in applications or web servers.
Prevention- Increase webserver connection limits: This can help reduce vulnerability to connection-based attacks.
54. Eavesdropping Attacks
Also known as “Traffic Interception,” this occurs when a third-party “listens” to info sent between a user and host. The kind of information stolen varies based on traffic but is often used to take log-ins or valuable data. An attacker intercepts communication between two parties to access sensitive information.
Prevention: Avoiding compromised websites (such as those not using HTML5) is an excellent proactive defense. Encrypting network traffic – such as through a VPN – is another preventive method.
55. Birthday Attack
A cryptographic attack exploits the birthday paradox to access a collision in a hash function. The attacker successfully generates two inputs to get the same output hash value. This can be used to compromise to bypass access controls.
Prevention-
- To prevent the birthday attack, the duration output for the hashing algorithm of the signature scheme might be chosen to be big enough that the birthday attack gets computationally impractical.
- In addition to using the longer bit length, the signer can avoid the attack by making some innocent but random alterations to the document before signing it and keeping the contract copy in their possession. They can demonstrate inside the court that the sign matches the agreement.
56. Corporate Account Takeover (CATO)
Hackers use stolen login credentials to access others' bank accounts.
Prevention-
- Use secure authentication methods for any sensitive areas of your site
- Ensure multi-factor authentication (MFA) or secure passwords
Impact of Cyber Attacks
A lack of focus on cybersecurity can most often cause serious damages in various ways including:
- Economic costs: This involves theft of intellectual property, corporate information, disruption in trading and the cost of repairing damaged systems.
- Reputational costs: This includes losing consumer trust and future customers to competitors due to poor media coverage.
- Regulatory costs: GDPR and other data breach laws can cause an organization to suffer regulatory fines or sanctions due to these cybercrimes.
Given the nature of these types of cyber attacks, it is vital for all businesses, regardless of the size, to understand cybersecurity threats and methods to mitigate them. This includes regular training on the subject, and a framework to work with – that aims to reduce its risks of data leaks and breaches.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
Cyber Attack Statistics
What are the costs and impact of types of cyber attacks for businesses?
The global cost of cyber attacks is expected to grow by 15% per year and reach over $10 trillion. A growing part of this cost is Ransomware attacks, which now cost businesses in the US $20 billion per year.
The average cost of a data breach in the US is $3.8 million. Another alarming statistic is that public companies lose an average of 8% of their stock value after a successful breach.
How well are organizations prepared for various types of cyber attacks?
In a recent survey, 78% of respondents said their company’s cybersecurity measures must be improved. As many as 43% of small businesses do not have any cyber defenses in place. At the same time, organizations of all sizes face a global cybersecurity skills shortage, with almost 3.5 million open jobs worldwide and 500,000 in the US alone.
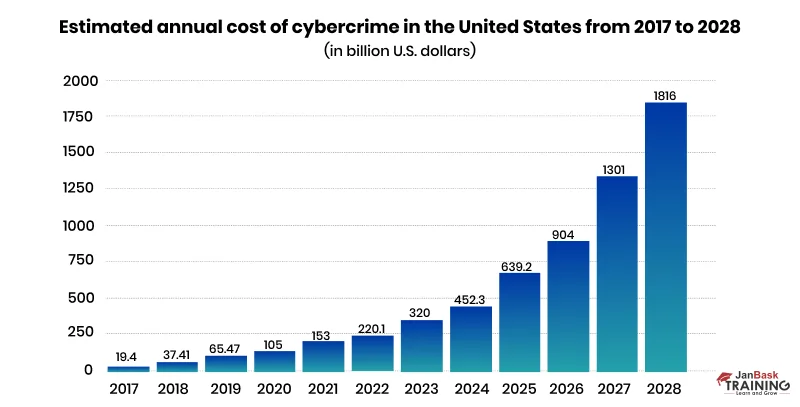
Cybercrime costs in the United States reached an estimated 320 billion U.S. dollars as of 2023. Between 2017 and 2023, this figure has seen a significant increase of over 300 billion U.S. dollars. According to the latest estimates, this dynamic will continue in upcoming years, reaching approximately 1.82 trillion U.S. dollars in cybercrime costs by 2028. The figures are disturbing and one might as well think how to learn cyber security to be safe from these types of cyber attacks and data breaches.


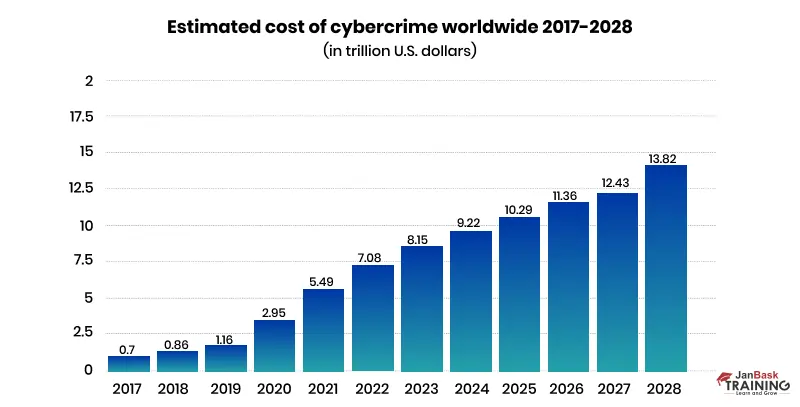
The global indicator 'Estimated Cost of Cybercrime' in the cybersecurity market was forecast to continuously increase between 2023 and 2028 by a total of 5.7 trillion U.S. dollars (+69.94 percent). After the eleventh consecutive year of increase, the indicator is estimated to reach 13.82 trillion U.S. dollars and, therefore, a new peak in 2028. Notably, the cybersecurity market's indicator, 'Estimated Cost of Cybercrime,' has continuously increased over the past few years.
This is why cyber security is critical, and so are cyber security professionals. The jobs in cybersecurity are in high demand. Check out the next section on how to learn cyber security, the job profile, and the current trend.
Cyber Security Career Scope
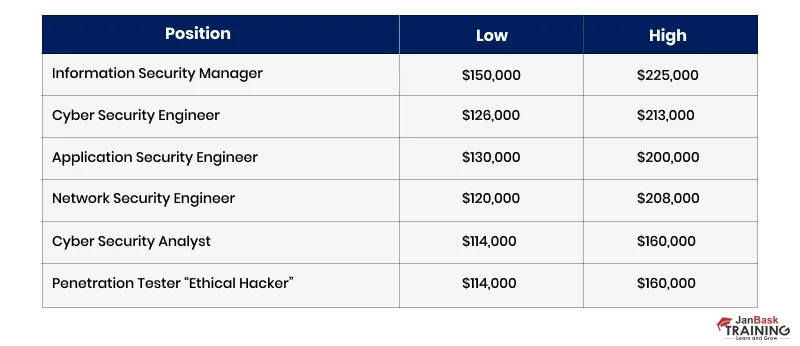
Let’s look at the six highest-paid cybersecurity jobs and their average cybersecurity salary ranges so you have the salary insights and take the next step to become one.

According to the US Bureau of Labor Statistics (BLS), the number of cybersecurity jobs is expected to increase by 35 percent between 2022 and 2032. This growth equates to 56,500 job openings per year for the next decade. Check out the cyber security career path that will help you decide and make vital decisions regarding your future.
As you read, there are 79,000+ Cybersecurity Jobs Available Worldwide, which is increasing. Tempted?
If you are still questioning how to learn cyber security, check out these fantastic cyber security courses that can help you master cybersecurity and move you up in the success ladder.
|
Courses
|
Details
|
|
EC Council Accreditation - Cyber Security Training & Certification
|
The EC-Council accredits our comprehensive Cyber Security Training course, which governs every standard of imparting the best-in-class education. The course will help build a strong foundation in the cybersecurity domain. You will learn about many Cybersecurity essentials like cyber security basics, cryptography, network security, how to secure an app, data Security, user Security, Cyberattacks, user access & identity management. So, register and get certified with us today!
|
|
New Age Online CISSP Training & Certification
|
Our CISSP training program is specially designed to give you deeper insights into the information security domain. The course will help you to learn the critical concepts of IT security, security architecture, design, management, and control. The JanBask CISSP (Certified Information Systems Security Professional) training will enable you to be an evangelist and champion in the agile adoption journey for the organization.
|
|
Certified Ethical Hacking Training & Certification
|
Our Ethical Hacking course will train you on the best practices hackers use to write codes. It will help you to protect your company from security breaches better. Also, you will master advanced network packet analysis, making web servers more secure, dealing with malware threats, or learning advanced system penetration techniques for building a highly secure network within industries.
|
How to Mitigate Against Different Types Of Cyber Attacks
The number of cyber attacks is increasing rapidly in different varieties and complexities. There are numerous preventive measures to follow for each kind of cyber attack. Besides, security practices and basic IT hygiene are other effective techniques to mitigate these types of cyber attacks. The best way to learn cyber security is to opt for trending cyber security courses and earn cybersecurity certification.
Apart from implementing effective cybersecurity practices, your organization should practice securing coding practices and keep systems and security software using firewalls and threat management tools.
Install antivirus software in your systems, control the access and user privileges, backup systems often, and proactively monitor the breached systems with a proper detection and response service.
Cyber Security Training & Certification
- Personalized Free Consultation
- Access to Our Learning Management System
- Access to Our Course Curriculum
- Be a Part of Our Free Demo Class
Conclusion
As a business owner or an individual, you may experience some of the types of cyber attacks mentioned above. It is alarming how easily sensitive data, accounts, passwords, and other items can be lost, erased, or exposed by types of cyber attacks. Tech firms are not safe from the threat. A security breach at Facebook exposed hundreds of millions of user records on an Amazon cloud server.
Cyber threats can cause considerable loss. That's why you must stand up and defend yourself and the business from the damage they cause. The best way to learn cyber security is to opt for trending cyber security courses and earn cybersecurity certification. Join the cyber security course offered by JanBask Training if you want to pursue a profession in advanced cyber security.
Frequently Asked Questions
Q1. How can you defend against a cyber attack?
Ans:- Here are a few ways to protect your business from the cuber security attacks –
- Adopt strict security measures.
- Enable multi-factor authentication and use strong passwords.
- Keep your OS and software updated.
- Post minimum personal information on social media.
- Never download or open links that you see in shady emails, apps, or text messages.
Q2. How do cyber security network attack takes place?
Ans:- There are two main ways that cyber attack occurs –
- Hackers locate security flaws or vulnerabilities in the system and try to use them
- Cybercriminals cheat users and make them reveal their private information so they can access the network and plan various types of cyber attacks
Q3. What to do in the event of a cyber attack?
Ans:- First of all, contact the Security IT department as soon as the cyberattack has been verified so they can keep an eye on the breach and determine what data has been exposed. Keep an eye on your accounts, update your login information, and alert the appropriate authorities.
Q4. What are the major four types of cyber attacks?
Ans:- There are various types of cyber threats. Some of the major cyber security attacks incudes malware attack, password attack, phishing attack, and SQL injection attack.
Q5. What is spoofing in cyber security?
Ans:- Spoofing in cyber security is a technique used by cybercriminals to pose as a reputable or well-known source. Spoofing can take many different forms, including faked emails, calls, DNS spoofing, GPS spoofing, websites, and emails.
Q6. What is phishing in cybersecurity?
Ans:- Phishing is the act of an attacker trying to get a user to do "the wrong thing," such as opening a malicious link or visiting a dubious website.
Q7. What is malware attack in cyber security?
Ans:-Malware attacks are frequent cyberattacks in which the victim's system is compromised by malware, which is typically malicious software. Ransomware, malware, command and control, and other specialized types of cyber attacks are all included in malicious software, sometimes known as viruses.
Q8. What is DoS cyber security?
Ans:-The term "denial of service" or "DoS" refers to a class of cyber security network attack whose main objective is to make a service unavailable. Since these are usually covered by the media, the DoS attacks that are most well-known are those that target well-known websites.
Q9. What are the latest types of cyber attacks?
Ans:- Following are some of the latest types of cyber attacks:
- TikTok Denies Cyber Attack.
- NATO Data Leak.
- Killnet DDoS Target Airports.
- Advocate Aurora Health Data Leak.
- Microsoft 2.4 TB Data Leak.
- Optus Exposes 2.1M Customers.
- $570M Binance Coin Hack.
- Uber's Systems Compromised.
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
1 day 19 Sep 2025
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
4 days 22 Sep 2025
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
1 day 19 Sep 2025
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
1 day 19 Sep 2025
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
1 day 19 Sep 2025
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
8 days 26 Sep 2025
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
7 days 25 Sep 2025
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
8 days 26 Sep 2025
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
2 days 20 Sep 2025
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
16 days 04 Oct 2025
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
29 days 17 Oct 2025
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
8 days 26 Sep 2025



 Businesses that need more safeguards in place risk sailing in waters where cybercriminals thrive in today's rapidly changing cyber security scenario. Every company must develop preventative best practices to deal with constantly changing threats and significant data breaches and should be thinking about how to learn cyber security to avoid all types of cyber attacks.
Businesses that need more safeguards in place risk sailing in waters where cybercriminals thrive in today's rapidly changing cyber security scenario. Every company must develop preventative best practices to deal with constantly changing threats and significant data breaches and should be thinking about how to learn cyber security to avoid all types of cyber attacks.























Phoenix Robinson
I wanted to know about the Cybersecurity attacks and how to work on them and your post really helped me understand well.
JanbaskTraining
Hi, Glad to know that you found this post helpful! For more insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Lane Clark
It’s a very informative blog, a must-read for people who want to be aware of the Cybersecurity Attacks.
JanbaskTraining
Glad you found this useful! For more insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Josue Rodriguez
Hey, is there any separate guide you can help me prepare for Cybersecurity related certification courses?
Colin Rodriguez
Earlier I thought that the job opportunities after graduation were not properly explained in a few places, and after reading this post, I got to know the different factors.
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here, and we will get back to you shortly!
Rafael Lewis
How to choose the best one among the numerous courses after graduation?
JanbaskTraining
Glad you found this useful! For more insights on your favorite topics, do check out JanBask Blogs and keep learning with us!
Kyle Lee
Wow! So many Cybersecurity ideas. I could learn a lot. Can anyone with an undergraduate or high school diploma join the training? If yes, then whom to contact?
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here, and we will get back to you shortly!
Riley Walker
Wow! I learned a lot about this blog. I want to explore a few best Cybersecurity related courses for career growth, but confused about which one is better, I want to consult a Janbask consultant on this.
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here, and we will get back to you shortly!
Jorge Hall
Hi, it's a lovely blog about the Cybersecurity Attacks. Now I am 200% times more motivated to pursue this skill as a career. But do you provide Cybersecurity Training?
JanbaskTraining
Hi, Thank you for reaching out to us with your query. Drop us your email id here, and we will get back to you shortly!
Beckham Allen
These are quite insightful for beginners like me. Please let me know a bit more about Cybersecurity Attacks.
JanbaskTraining
Hey, thank you so much. We are grateful that our blog has been a help to you! For further insight do connect with us at https://www.janbasktraining.com/contact-us
Cayden Young
Excellent blog! I was confused about the concept of Cybersecurity Attacks. But, after reading this blog I have got a lot of ideas.
JanbaskTraining
Hey, thanks for sharing the feedback. We hope our blog has assisted you in making better decisions. For further assistance, you can connect to us at https://www.janbasktraining.com/contact-us