Introduction
Cybersecurity risks exist, and the frequency of cyberattacks grows substantially year after year. At the same time, customers are becoming more aware of the dangers of cybersecurity and demanding greater performance from the businesses they do business with. Consumers share this sentiment, and regulators respond with increasingly rigorous data privacy requirements.
A strong cybersecurity architecture has never been more critical for these reasons. In this post, we'll define cybersecurity architecture, explain why it's vital, discuss a cybersecurity architect's role, cybersecurity architect certifications and training, etc.
Who Is A Cyber Security Architect?
A cybersecurity architect has the knowledge, abilities, and expertise to build and implement a secure cyber architecture for a company.
A cyber security architect's responsibility is to guarantee that all IT infrastructure components are secured from potential threats. These dangers may originate from hackers or malware programs, but accidental hardware or software damage is the most common threat.
This means that a cyber-security architect must be able to foresee how hackers can target their systems and ensure that measures are in place to prevent this. They must also be able to discover any vulnerabilities in their network and ensure that they are addressed as quickly as possible.
A cybersecurity architect is responsible for planning, designing, testing, implementing, and maintaining a company's computer and network security infrastructure. This senior-level position necessitates a solid understanding of the employer's business and the technology used to perform operations.
Some of the main characteristics of a successful cybersecurity architect are:
- The ability to think like a malicious hacker in order to foresee and defend against information security dangers.
- Capability to think like a business executive, manage security team members, and effectively interact with key stakeholders.
- The ability to develop security infrastructure from the ground up or update existing systems in response to continuing changes in the security landscape, such as new risks and adherence to applicable rules.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
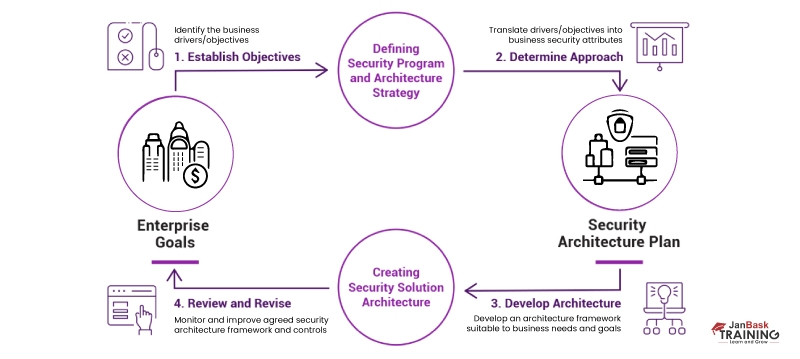
How To Build An Effective Cybersecurity Architecture
Creating computer systems to ensure the security of your underlying data is known as cybersecurity architecture, also known as network security architecture. Cybersecurity architecture is the solid foundation of an organization's defense system against security threats.

Cybersecurity architecture is typically designed using a cybersecurity architectural framework specifying a computer network's structure, standards, policies, and functional behavior, including security measures and network features.
Cybersecurity architects will design a framework that will assist your organization in identifying security threats and putting security measures in place to address them. It will also demonstrate the relationship between your security procedures and your overall business. A cybersecurity architecture framework enables your organization to preserve confidentiality, integrity, and availability of important and critical information inside its business activities.
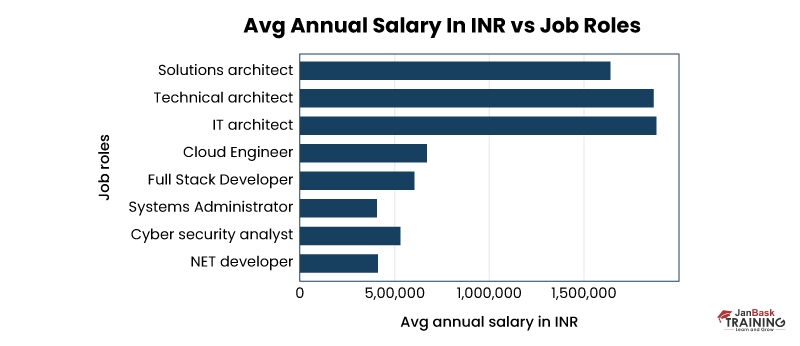
Salary and Career Prospects for a Cyber Security Architect

You may be wondering about the importance of cybersecurity architecture. You may have many questions; for example, what is the compensation of a cybersecurity architect? Is there a high demand for cybersecurity architects? What about the perks and advantages?
According to Infosec Report , the average salary of a cybersecurity architect is USD $134,815. Of course, this will vary depending on your region, years of experience, and the nature of your relevant skillset. Along with the good pay scale, a cybersecurity architect receives great health benefits and may be eligible for incentives and profit-sharing.
Given that cybersecurity is the top priority for CEOs in the United States, it's no surprise that the need for cybersecurity architects is increasing. Concerns about cybercrime have grown in recent years due to several high-profile cybersecurity incidents.
According to the Information of the Bureau of Labour Statistics, cybersecurity employment is expected to rise by 27% between 2022 and 2024. Furthermore, there appears to be a rising skills gap in the industry as baby boomers retire and millennials fail to replace them at a comparable rate.
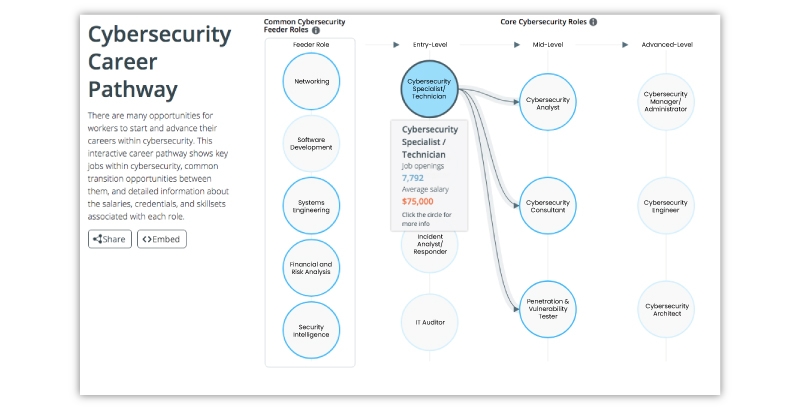
Career Outlook of Cyber Security Architect

The number and job types increase as the cyber security industry develops and grows. The industry is growing more specialized. It's also starting to get really interesting and exciting. This means that if you are entering the realm of cyber security right now, you may do it virtually on the first floor of a thriving industry. Although many seasoned professionals may act as mentors, it will still be your responsibility to develop this industry for future generations.
Associate Security Consultant: The starting salary for this position is $80,827 per year, and the maximum annual salary is $144,500. You'll need to conduct penetration testing, forensic investigations, and incident response. Those with demonstrated talents are welcome to apply, as no formal education is listed as a qualification for this post.
Internship in Network Technology: This paid internship costs up to $38.86 Per Hour. You must be enrolled in a bachelor's, master's, or MBA program with a concentration in one of the following areas: computer science, statistics, information technology, project management, or a closely related discipline.
Cyber Security Risk Analyst: If becoming a cyber security architect is your long-term aim, you must excel as a cyber security risk analyst. The employer requires a bachelor's degree in computer science or a closely related discipline. You should be an expert in solutions design, application development, penetration testing, and cryptography, among other things if you want to succeed and get the position.
Skills of Cybersecurity Architect

CSOonline provides an excellent summary of the requisite abilities and competencies for this post in a story that dissects the job description of an information security architect. The following are essential requirements:
Experience
- Designing and implementing security solutions using emerging technologies; monitoring and enhancing such solutions while working with an information security team.
- Consulting and engineering in the creation and development of best practices for security; putting security measures in place to fulfill corporate objectives, customer expectations, and legal requirements.
- Cloud computing security issues include data breaches, hacking, account hacking, third parties, authentication and verifications, APTs, data loss, and DoS attacks.
- Identity and access management entails tracking and developing/enforcing policies that regulate access to sensitive technological resources and information assets.
General Abilities
- Excellent communication abilities; good critical thinking and analytical abilities
- Strong leadership, project management, and team-building abilities, as well as the ability to lead teams and drive initiatives across different departments
- Capable of identifying hazards in company processes, operations, technological initiatives, and information security programs.
- Capability to act as an enterprise security subject matter expert capable of explaining complex topics to others without a technical background.
Technical knowledge and abilities:
- Operating systems, including Windows, UNIX, and Linux
- Cybersecurity training and online courses/classes
- Comprehensive knowledge of VB.NET, Java/J2EE, API/web services, ColdFusion, scripting languages, and relational database management system (RDBMS) such as MS SQL Server or Oracle are the most important programming languages for hacking courses..
- Comprehensive knowledge of essential industry security standards and protocols, such as ISO27001 and the National Institute of Standards and Technology (NIST); Control Objectives for Information and Related Technologies (COBIT); Treadway Commission Committee of Sponsoring Organisations (COSO), a cooperative endeavor to combat corporate fraud
- ISO 27001 information security management system standards
- Wireless security; router, switch, and VLAN security
- Procedures for risk assessment, policy development, role-based authorization approaches, authentication technologies, and security attack patterns
Role of a Cyber Security Architect

Now that you know of the demand for cybersecurity architect and their perks, i.e. their high payscale and skills required to pursue your career as a cybersecurity architect. Let us know about their job responsibilities. Among the functions and responsibilities of a cybersecurity architect are:
- Gaining a thorough understanding of the organization's information and technology systems
- Planning, researching, and building security architectures that are dependable, powerful, and adaptable for all IT projects
- Conducting vulnerability testing on the completed infrastructure, as well as risk analysis and security assessments
- Investigating the new standards and systems of security, and authentication procedures
- Defining, developing, implementing, and maintaining all necessary business security policies and procedures, as well as ensuring that all workers follow them
- Creating specifications for all IT assets, such as routers, firewalls, local area networks (LANs), wide-area networks (WANs), virtual private networks (VPNs), and any other network equipment.
- Examining and authorizing the installation of all firewalls, VPNs, routers, servers, and intrusion detection systems (IDS).
- Critical public infrastructure (PKI) design includes digital signatures and certification authority (CA)
- Testing the organization's final security architecture to ensure they work as expected.
- Technical direction and management for security teams
- Managing any security awareness programs and training activities aimed at better preparing non-IT staff
- Responding swiftly to any security-related problems (e.g., data breaches, viruses, phishing scams) and giving a comprehensive post-event review once a resolution has been reached
Certifications and Educational Requirements for Cybersecurity Architects
Certifications are critical in the cybersecurity business because they teach new skills, allow IT professionals to expand on their experience and expertise, and certify competency levels to prospective employers.
Among the most significant cybersecurity architect courses and associated career credentials are:
- CISSP (Certified Information Systems Security Professional): The CISSP certification includes IT architecture definition and designing, constructing, and managing a safe business environment utilizing globally accepted security standards. This program also covers industry best practices, so you'll be ready for the CISSP certification exam.
A CISSP certification certifies your IT security knowledge. According to Cybersecurity Ventures, there will be 3.million Cyber Security jobs available by 2024. The global Cyber Security industry is assumed to have revenues of USD $282.3 billion by 2024, with an 11.1 percent annual growth rate.
- CISM (Certified Information Security Manager): The CISM certification supports international security practices and recognizes the person who manages, designs, oversees, and assesses an enterprise's information security. The CISM certification is the globally recognized level of achievement for authorized information security management professionals, and it is in high demand.
- CISA (Certified Information Systems Auditor): The Certified Information Systems Auditor (CISA) certification course teaches you how to administer and oversee enterprise IT and perform an efficient security assessment.
CISA is one of the most desired and popular certification courses for audit, control, and security skill professionals in information systems.
- GDSA (GIAC Defensible Security Architecture): A professional certification called the GIAC® Defensible Security Architecture (GDSA) demonstrates that a person can design, implement, and tune an effective combination of network and data-centric controls to balance prevention, detection, and response."
A group of vendor-neutral computer security certifications from GIAC is tied to the SANS training programs. In order to stay abreast of "black hat" methods, GIAC focuses specifically on cutting-edge technological advancements in IT security.
Regarding academic attainment, most organizations need security architects to have a bachelor's degree or above.
The Advantages of Cybersecurity Architect Certification and Training
Cyber security architects can obtain certification by undergoing training in a specific subject by enrolling in a course (or courses), completing all of the required tasks and by passing a certification exam. Cybersecurity certification and training are important since they provide written, quantitative proof that they know what they're discussing.
For this reason, most firms and organizations seek certification. When they see that they're certified and competent in doing the job for which they're recruiting them. That’s why obtaining certification is vital part of cybersecurity architect training.
Cyber Security Training & Certification
- Personalized Free Consultation
- Access to Our Learning Management System
- Access to Our Course Curriculum
- Be a Part of Our Free Demo Class
Closing thoughts
Cybersecurity architects are especially adept at detecting possible dangers. They understand computer and network systems well enough to build security architecture strategies, implement them, and monitor their success.
CyberSecurity architect can assist your organization by providing qualified security specialists to your IT department to handle your future cloud architecture installation. With our cybersecurity tutorial, you can become a specialist that can configure a secure network using the most recent best practices and assist any organization with whatever technology it employs.
FAQs
Q1. What is the meaning of the prefix cyber-?
Ans:- The cyber- prefix often refers to cyberspace, the virtual world composed of all networked computers, the interconnections of which create the Internet-of-Things (IoT). In the context of cybersecurity (= cyber + security), for example, it is usual to refer to cyber threats, cyber attacks, cyber defences, and cyber countermeasures.
Q2. What is the process of cybersecurity?
Ans:- When organisations rigorously practise excellent cyber hygiene practises while concurrently checking their cyber defence vulnerabilities defences via aggressive white hat" (a.k.a. "ethical hacking"), cybersecurity technology and processes are most effective.
Q3. What is the most effective technique to study cybersecurity?
Ans:- The ideal way to study cybersecurity and other technologies is to blend theory (principles and practises) with hands-on best practises. If you don't have immediate access to a cybersecurity expert, look into the cybersecurity training services on this website's Cybersecurity Training page.
Q4. What qualifications do cybersecurity professionals require?
Ans:- As computer and network technology evolves, so will the abilities, practises, and technologies you'll utilise as a cybersecurity professional. Your eagerness to study, problem-solving skills, and attention to detail will serve you well in this career. Other more technical skills and technologies to learn are as follows:
- SIEM (security information and event management) tools
- Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), and Firewalls
- Computer forensics
- Management of mobile devices
- Data administration
- Development of application security
- Audit and compliance expertise
Q5. What does cybersecurity architecture serve?
Ans:- The goal of accurately and exhaustively designing a cybersecurity architecture is to ensure that the underlying network architecture is properly protected from existing and future cyber threats, including its crown jewel sensitive data and key applications.
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
0 day 19 Sep 2025
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
3 days 22 Sep 2025
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
0 day 19 Sep 2025
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
0 day 19 Sep 2025
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
0 day 19 Sep 2025
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
7 days 26 Sep 2025
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
6 days 25 Sep 2025
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
7 days 26 Sep 2025
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
1 day 20 Sep 2025
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
15 days 04 Oct 2025
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
28 days 17 Oct 2025
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
7 days 26 Sep 2025