Introduction
Have you ever encountered a website that takes forever to load, or is completely inaccessible? DDoS attacks might be the culprit. This tutorial dives deep into the world of DDoS attacks, answering all your questions:
- What exactly is a DDoS attack?
- How can you identify one?
- What are the different types of DDoS attacks?
- Is it legal to launch a DDoS attack?
- How can you protect yourself and your devices?
We'll also explore the attacker's perspective, but for purely educational purposes. This knowledge will empower you to understand and defend against these malicious attempts.
Let's get started!
What is a DDoS Attack?
A Distributed Denial-of-Service (DDoS) attack aims to disrupt an online service by overwhelming it with a flood of traffic from multiple sources. These attacks target critical resources, like banks and news websites, making it difficult for people to access important information.

DDoS is flooding the target with a constant flood of traffic.
Read: Factors That Increase Your Cyber Security Salary - Complete Guide
Imagine a web server for a company that sells products online. Customers with computers browse the website to view products and services. If someone wanted to attack this company's server, they might use a program to flood the server with data traffic, disrupting its service. This is a Denial-of-Service (DoS) attack, originating from a single source. DoS attacks are easier to handle because the server can identify and block the attacker's connection.

DoS(Denial of Service) Attack

DDoS(Distributed Denial of Service) Attack
Imagine a single lane road leading to a popular amusement park. Normally, traffic flows smoothly. But what if a bunch of cars, more than the road can handle, suddenly try to use the road at the same time? This creates a traffic jam, blocking everyone from reaching the amusement park.
This is similar to a DDoS attack. In the digital world, instead of cars, a flood of fake requests overwhelms a website or server. These requests come from many different computers, just like the cars in the traffic jam. The website or server gets overloaded and can't respond to real users trying to access it, effectively denying them service.
Just like you might be stuck in traffic and unable to reach the amusement park, legitimate users can't access the website or server under a DDoS attack.
This explanation avoids technical terms and focuses on the core concept of overwhelming a system with too much traffic. It uses the relatable analogy of a traffic jam to make the idea of a DDoS attack easier to understand.
How to identify a DDoS attack?
DDoS Attack Symptoms
The most obvious symptom of a DDoS attack is when a site or service suddenly starts behaving lethargic, becoming too slow or unavailable. There might be a possibility that the site may start reacting gradually. But such a legitimate spike in traffic — can create similar performance issues, so need to be investigated because any kind of such interruption, contingent upon your setup, can be crushing to your business.
The symptoms of DDoS assaults include:
- The site is reacting gradually
- The site is lethargic
- The client has issues getting to the site
There are other, more specific signs of DDoS attacks that can vary depending on the type of attack.
Online Traffic analytics tools can help you spot some of these attack indication signs of a DDoS, these tools can help you get aware of :
- Suspicious amounts of traffic originating from any single IP address
- Repeated traffic from users who share the same behavioral profile, such as device type, geolocation, or web browser version
- An unexplained surge in requests to a single page or endpoint
- Unnatural or Odd traffic patterns such as spikes at odd hours of the day (e.g. a spike every 20 minutes)
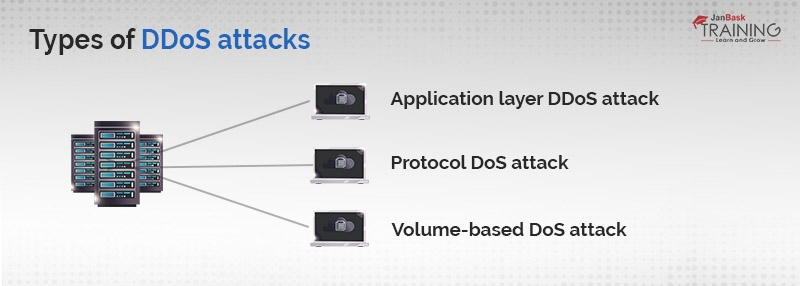
Types of DDoS Attacks
Now that we understand DDoS attacks, let's delve deeper into different types of DDoS attacks. DDoS attacks can be broadly categorized into three main groups:
- Application Layer Attacks: These attacks target vulnerabilities in specific software like Windows, Apache, or OpenBSD to exploit the server and cause crashes.
- Protocol Layer Attacks: These attacks target the communication protocols used for network traffic. Examples include SYN floods, Ping of Death attacks, and more.
- Volume-based Attacks: These attacks overwhelm the target with a massive amount of traffic, such as ICMP or UDP floods, using spoofed packets.
While DDoS attacks are the most well-known, there are other methods attackers can use to disrupt a website:
- Teardrop Attacks: These attacks send fragmented and oversized data packets to overwhelm the target system, causing crashes.
- Banana Attacks: These attacks create a feedback loop by sending messages from the target back to itself repeatedly, overloading the system.
- Smurf Attacks: These attacks exploit weaknesses in network devices to amplify traffic and overwhelm the target.
- Permanent Denial-of-Service (PDoS) Attacks: These attacks involve compromising and manipulating firmware on Internet of Things (IoT) devices to disrupt their functionality.
- Nuke Attacks: Attackers send corrupted data or malicious code to crash the target system.
- Peer-to-Peer Attacks: Hackers compromise a system and instruct all connected devices to flood a specific website or server.
- Ping Floods: Attackers bombard a target with a constant stream of ping requests, overloading its resources.
- Degradation-of-Service Attacks: These attacks use botnets to launch waves of attacks, causing the target to slow down significantly without completely shutting down.
- HTTP POST Attacks: These are outdated attacks that involve sending large amounts of data slowly, tying up resources and preventing other requests from being processed.
- Denial-of-Service Level 2 Attacks: These attacks bypass security measures by targeting the network layer, potentially taking the entire network offline.
- Ping of Death Attacks: These attacks send oversized ping packets (larger than 65,535 bytes) that can crash vulnerable systems.
- Amplification Attacks: These attacks exploit weaknesses in open DNS servers to redirect large volumes of traffic towards the target.
- Slowloris Attacks (or RUDY attacks): These attacks attempt to establish as many connections to a server as possible for extended periods, hindering access for legitimate users.
- Shrew Attacks: These attacks exploit weaknesses in the TCP protocol to disrupt legitimate traffic flow.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
How do the attackers get involved in a DDoS attack?
The simple answer to this question is by simply using malicious software. The attacker or the intruder will develop malware and distribute it over the internet and put it on websites or email attachments.
Thus, if a vulnerable computer goes to these infected websites or opens these infected email attachments, the malware will be installed on their computer without the knowledge of the owner that the computers have gone infected or without knowing that their computers have been recruited in an army of other infected systems to perform a DDoS attack. This army of affected computers is known as a botnet. This botnet can be even hundreds or thousands of computers that are scattered all over the world. This botnet is controlled like an army waiting to receive instructions from the attacker. The attacker gives the command to the botnetto attack on a certain date and at a certain time. Once the set time is reached the attack begins!

A DDoS attack can last for an hour or even days. It just depends upon the intender’s intent. Indeed, a review by Kaspersky Lab uncovered that one out of five attacks can keep going for a considerable length of time or even weeks, bearing witness to their refinement and genuine danger presented to all organizations.
The impact of the attack is that during that, no workers can get access to the network resources, and on account of Web servers running eCommerce locales, no buyers will have the option to buy items or get help. The dollar figure fluctuates, however organizations can lose $20,000 every hour in case of an effective attack.

DDoS attacks are surprisingly cheap and easy to initiate, that is, one can easily slow down any website anywhere in the world by buying its cheap services. Slow and independent sites are at particular risk. Because the relative flood of traffic can be taken offline as they don’t tend to have resources or infrastructure to defend themselves. Intruders take advantage of this vulnerability by using DDoS attacks to influence political events and some opposing media.
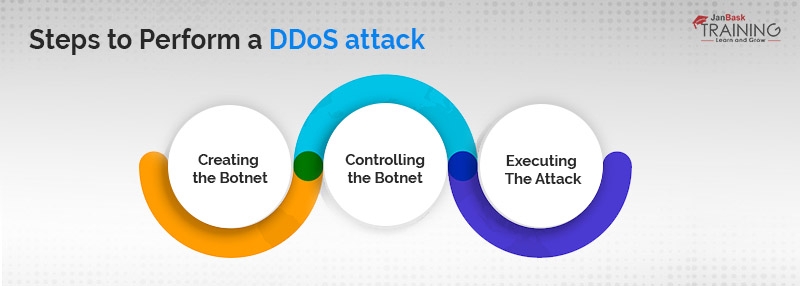
How DDoS is performed?

Stage 1: Creating the Botnet
To create a botnet, a hacker needs an approach to assume responsibility for a great many gadgets — these could be PCs, cell phones, or IoT gadgets, for example, webcams or brilliant fridges. There are many ways the hacker could discover and assume responsibility for these gadgets. For instance, they may compose an infection that proliferates and progressively assumes control over an ever-increasing number of PCs. Or on the other hand, they may locate a particular IoT gadget with known helplessness (for instance, poor default login security) and construct a bot to examine the web and hack however many of those gadgets would be prudent.
Stage 2: Controlling the Botnet
As the programmer assumes responsibility for every gadget, they'll accomplish something so it will comply with any directions the programmer sends to the gadget. (For instance, installing a small program on it.) There are a couple of various methodologies the programmer can utilize (customer server model, P2P model dependent on advanced endorsements, and so on.), yet the final output is the equivalent — the hacker can give an order and every one of the gadgets in the botnet will do whatever the hacker educated them to do.
Stage 3: Executing the Attack
Once the hacker has a huge number of gadgets available to him no matter what, he can execute the DDoS attack. There are a couple of various kinds of DDoS attacks (read them below). However, the essential thought is the equivalent: flood a web server with a larger number of solicitations than it can deal with. The aggressor will normally inquire about the objective site cautiously to distinguish a shortcoming to abuse, at that point create a solicitation that will focus on that powerlessness. At last, the assailant will train their zombie PCs to execute that solicitation (more than once). Here's a model: Let's say John's botnet has 100,000 gadgets in it. He gives an order to the botnet to send an HTTP solicitation to example.com once every second. That is 60 visits for each moment times 100,000 gadgets. That signifies 360 million visits for every hour or 8.6 billion visits for every day. That is definitely more than most web servers are intended to deal with. If the assault was arranged well, the webserver will be over-burdened and any genuine individuals who attempt to visit the webpage will get a blunder message. DDoS assault achievement!
Read: Cybersecurity Certifications
“You can buy a week-long DDoS attack on the black market at $150 only”
Is it legal to perform DDoS?
Legally: Launching a DoS attack against an organization or website is generally considered a crime, although the severity can vary. In most cases, you'd face jail time (around a year) and a hefty fine.
The Complications:
- Severity of Impact: The consequences worsen if your attack causes significant damage, like targeting emergency services. Additional charges might apply.
- Arguments for Legality: Some claim DoS attacks can be a form of protest. However, getting caught will still lead to legal trouble.
- Government Use: Governments sometimes use DoS attacks in cyberwarfare, creating a legal gray area.
- Internal Testing: Organizations may launch controlled DoS attacks to test their own server defenses.
The Bottom Line: Don't launch DoS attacks. They're illegal and can land you in serious trouble.
However: It's important to understand the complexities surrounding DoS attacks and their potential justifications in specific situations (like government use).
How are DoS/DDoS attack tools categorized?
There are a number and different types of tools that are explicitly designed for to launch DoS/DDoS attacks
Types of DDoS Tools
Low and slow attack tools
As the name implies, these types of DDoS attack tools are used for low volume of data and operate very slowly, specifically designed to send small amounts of data across multiple connections in order to keep ports on a targeted server open as long as possible. Low and slow attack tools continue to take up the server's resources until it is unable to maintain additional connections.
Application layer (L7) attack tools
Application layer (L7) attack tools are used to target layer 7 of the OSI model, where HTTP. Using this a malicious actor can launch attack traffic that is difficult to distinguish from normal requests made by actual visitors.
Protocol and transport layer (L3/L4) attack tools
Protocol and transport layer (L3/L4) attack tools utilize protocols like UDP to send large volumes of traffic to a targeted server, such as during a UDP flood and are often ineffective individually.
Let’s see some amazing DDoS Tool...
Best 10 DDoS Attacking Tools
Here is the list of top 1o best DDoS tools that you can go for-
- LOIC (Low Orbit ION cannon)
- DDoS Attacks or Solarwinds
- PyLoris.
- DDoSIM (DDoS Simulator)
- RUDY
- HTTP Unbearable Load King (HULK)
- HOIC (High Orbit ION cannon)
- GoldenEye.
- Tor's Hammer
- OWASP HTTP POST
After covering the best DDoS Attacking Tools, this DDoS blog is going to help you with the best practices to defend Dos/DDoS attacks. Before we move further, let’s quickly go through the JanBask Training Cybersecurity training options that can add feather in your career.
What Are Best Practices to defend against DDoS Attack?
DDoS attacks take a variety of forms, mitigating them requires a lot of niche knowledge and a variety of practices. In this DDoS Blog, next, we are going to talk about some best practices or tactics for stopping DDoS attacks-
- Know your network's traffic & understand your organization’s normal traffic pattern
- Create a Denial of Service Response Plan
- Make your network more resilient
- Practice good cyber hygiene & leverage best security practices
- Scale up your bandwidth to absorb a larger volume of traffic
- Take advantage of anti-DDoS hardware and software
- Moving to the cloud can mitigate DDoS attacks
- Know the symptoms of an attack and optimize accordingly
- Outsource your DDoS protection services
How to protect yourself from DDoS attacks?
Are unexpected outages causing headaches? DDoS attacks, where attackers flood your systems with traffic, could be the culprit. These attacks can crash your servers, costing you money and stressing your IT team.
Here's what you can do:
-
Be Prepared: Having DDoS mitigation strategies in place is crucial. This includes understanding how to identify and stop an attack before it overwhelms your systems.
-
Check Internally: First, confirm if the outage is due to scheduled maintenance or an internal network issue. Your network administrator can monitor traffic patterns to detect an attack, pinpoint its source, and take action. This might involve implementing firewall rules or rerouting traffic through a DDoS protection service.
-
Contact Your ISP: They can check for outages on their end or if their servers are the target, with you being impacted indirectly. They can also provide DDoS mitigation guidance specific to your situation.
-
Knowledge is Power: Learn about cybersecurity! Understanding how DDoS attacks work gives you an advantage. Consider ethical hacking courses to gain a comprehensive understanding of DDoS attacks, mitigation techniques, and how to defend yourself effectively.
By following these steps, you can protect your systems from DDoS attacks and minimize downtime.
Final Thoughts
So this was the complete DDoS how-to guide, hope you now have a clear understanding of what is DDoS attack and how to perform a DDoS attack. With the above, we have gained in-depth knowledge on what is DDoS, what is DDoS attack, types of DDoS attacks, how to perform a DDoS attack, and solutions for DDoS mitigation. If you have been looking for a DDoS tutorial for beginners, you can sign in for our Cybersecurity self-learning module. Also join the JanBask Training Community to get professional support from expert professionals and career guidance.
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
-0 day 19 Sep 2025
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
3 days 22 Sep 2025
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
-0 day 19 Sep 2025
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
-0 day 19 Sep 2025
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
-0 day 19 Sep 2025
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
7 days 26 Sep 2025
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
6 days 25 Sep 2025
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
7 days 26 Sep 2025
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
1 day 20 Sep 2025
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
15 days 04 Oct 2025
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
28 days 17 Oct 2025
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
7 days 26 Sep 2025