Introduction
If you’re confused between information security and cybersecurity, you’re not alone. These terms are often used interchangeably, and while they share a common foundation, their functions, goals, and implementations are quite distinct.
In this blog, we’ll break down the fundamental differences between information security and cybersecurity. You’ll gain clarity on each domain’s unique responsibilities, required skill sets, career opportunities, and earning potential—so you can confidently understand or pursue a path in either field.
Still wondering if one is more important than the other? Or which offers better career growth? Don’t worry—we’ll address all of that and more. By the end of this article, you’ll have a crystal-clear understanding of how cybersecurity and information security differ, how they overlap, and which direction might be the right fit for your career.
But before we dive into Information Security vs. Cybersecurity, let’s first understand each field individually to set the foundation.
Give this blog a thorough read to clear all doubts that linger in your mind and have no second thoughts on cyber security vs information security. If this blog piques your interest, you can even pursue a cyber security or information security career.

What is Information Security?
Information security is the practice of protecting information as well as information systems against unauthorized access, disclosure, disruption, destruction, modification, removal, or use. It generally focuses on the confidentiality, integrity, availability (CIA) aspects of the information.
- Confidentiality – Refers to preserving authorized restrictions on access and disclosure of information, including a means for protecting personal privacy as well as proprietary information.
- Integrity – Refers to defense against inappropriate information, destruction, or modification ensuring information authenticity and non-repudiation.
- Availability – Refers to ensuring reliable and timely access to information.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
What is Cybersecurity?
Cybersecurity protect networks, servers, electronic systems, computers, programs, and data from malicious cyber-attacks. These attacks are usually aimed at assessing, changing, or destroying sensitive information. It is also responsible for identifying critical data, its risk exposure, and the technology you must implement to protect information.
It also protects information and communications technologies, termed ICT (information and communications technology) security. You can explore this field and learn about Cybersecurity, its certifications, salaries, and job trends.
Information security vs Cybersecurity Based On Different Factors

How Information Security and Cybersecurity Differ In Definition
Information security is the process of protecting information as well as information systems against unauthorized access, disclosure, destruction, undesired modification.
Primarily focuses on information and ensures its confidentiality, integrity, and availability.
Whereas…
Cybersecurity refers to the practice of protecting data, its related technologies, and storage sources from malicious attacks. It is all about the cyber realm and the data associated with it.
How Information Security and Cybersecurity Differ In Domain
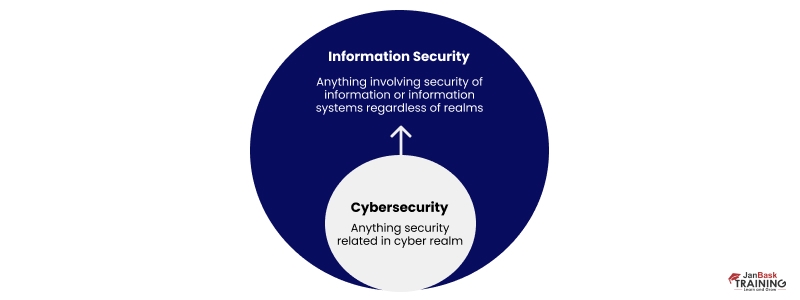
Information security deals with protecting both digital and analog forms of information regardless of the realm. It deals specifically with information assets and ensures integrity, confidentiality, and availability of information.
Whereas…
Cybersecurity deals with the protection of anything and everything present in the cyber realm, such as data, information, storage resource or devices, and associated technologies.
How information security and cybersecurity differ in Process
Information security simply protects information from any form of threat and forms the foundation of data security.
Whereas...
Cybersecurity primarily deals with protecting the use of cyberspace from advanced persistent cyber threats.
How Information security and Cybersecurity differ in Functionality
Information security deals with all forms of threats against information. Disclosure modification and disruption, and unauthorized access are the most important issues tackled by information security specialists.
Few more information security functionalities are:
- Procedural controls: These controls prevent, detect, or minimize security risks to any physical assets such as computer systems, data centers, involve security frameworks, compliance training, and more.
- Access controls: These controls regulate who is allowed to access and use company information, network, and resources.
- Technical controls: These controls involve using multi-factor user authentication, firewalls, and antivirus software.
- Compliance controls: These controls deal with privacy laws and cybersecurity compliances designed to minimize security threats.
Whereas…
Cybersecurity deals with all dangers lurking in cyberspace specifically cybercrimes, cyber frauds, and law enforcement. Also responsible for identifying critical data, and its risk exposure, and the required technology to protect it.
Few more cybersecurity functionalities are:
- Network security: the practice of securing networks against unauthorized access, misuse, interruption of network services.
- Application security: the process that involves detecting, fixing, and enhancing the security of applications.
- Cloud security: the process of protecting cloud-based infrastructures and systems
- Critical infrastructure: Set of antivirus tools that provide security services such as virus scanners, intrusion prevention systems, anti-malware software, and more.
Information security vs Cybersecurity: Career Outlook

If you are planning to join information security or cybersecurity career, you might have questions like….
- Which is better, cybersecurity or information security?
- What all skills & certifications are required for a shining security career?
- Is it possible to get into cybersecurity without a degree?
- How to get into a security career with no experience?
- What is the average salary for cybersecurity specialists?
How are These Security-Based Terms Related to Each Other?

Information security deals with protecting all forms of information regardless of the realm. While Cybersecurity deals with protecting anything and everything present in the cyber realm only. So, cybersecurity can be viewed as a subset of information security, ultimately both consider the value of the data and focus on data protection.
Both information security and cybersecurity personnel need to be aware of the scope and the shared mission to secure your organization.
The Must-Have Skill Sets For Information Security or Cyber Security Careers
If you want to plunge into a career in the security field and reach new heights, you will need to exhibit brilliant cybersecurity skills with specific domain knowledge and various soft skills. JanBask Training Cybersecurity courses can help you a lot during the process. Let’s examine the technical and non-technical skills needed to become an information security or cyber security expert.
Required Technical Skills
- SIEM Management
- Audit & Compliance
- Analytics & Intelligence
- Firewall/IDS/IPS Skills
- Digital Forensics
- Intrusion Detection
- Device Management
- Security Development
- Understanding of Hacking
- Security Incident Handling & Response
- Advanced Malware Prevention
- Data Management Protection
- Identity & Access Management
Required Nontechnical Skills
- Strong Leadership
- Passionate About Learning
- Analytical, Inquisitive, and Insightful
- Hyper Critically thinking
- Project Management
- Collaborative & Consultative
World-Class Certifications for Information Security and Cyber Security Career
Understanding technical security issues is critical for any cybersecurity or information security professional, regardless of the specific field of specialization. Understanding the differences between these two related but distinct fields can help individuals choose the most appropriate career options that match their goals and interests. Relevant top security certifications are sought after by employers, which will help you land a great job with a lucrative salary.

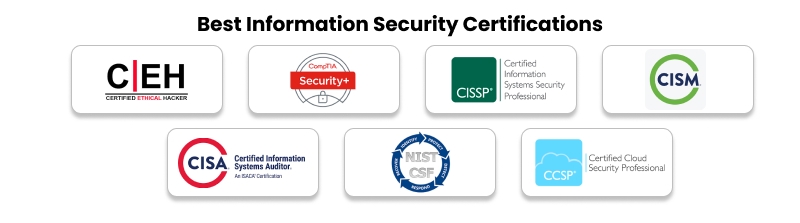
Best Information Security Certifications
Wondering about the best information security certifications? Don’t worry. A list compiled just for you mentions all the information security certifications. Let’s have a look.
Best Cyber Security Certifications
The best cyber security certifications are stated below that will give you a clear idea on why you should pursue this domain. Let’s have a glance at it.
- CISSP (Certified Information Systems Security Professional)
- GSEC: GIAC Security Essentials.
- ECSA: EC-Council Certified Security Analyst.
- GPEN: GIAC Penetration Tester.
- SSCP: Systems Security Certified Practitioner.
- Cyber Security- Master
- CRISC: Certified in Risk and Information System Control.
- CISA: Certified Information Systems Auditor.
Which is better, cybersecurity or information security as a career?
There might be a difference between cybersecurity and information security, but they are both are equally demanding and the fastest-growing careers need qualified security professionals, offering job opportunities with high median salaries, and a challenging, fast-paced work environment. Based on your interest and the above-highlighted differences, you can choose the suitable one.
How Can A Degree In Cybersecurity Or Information Security Be Helpful?
Grabbing a cybersecurity or information security degree can open the gates to entry-level and intermediate ranks, comprising computer and information systems management, information security analysis, and computer architecture. Look at the degrees you can earn from a cybersecurity or information security course.
1. Computer And Information Systems Manager
A computer and information systems manager is responsible for achieving company targets by collaborating on actions relevant to computer systems. You will also be required to detect issues and take the necessary steps to correct them. Apart from this, your duty is maintaining hardware and software, suggesting updates, examining and showing the budget to firm executives, and collaborating with other experts.
2. Information Security Analyst
They defend the computer system by generating security programs. You will be responsible for detecting and settling security breaches and probable problems. Researching fresh security programs, showing them to the hierarchy, helping to install security systems, and arranging reports related to security issues are also a part of your duty.
3. Computer Systems Analyst
Computer systems analysts produce solutions to issues underlying the computer system. You must find technology to refine the system’s speed and examine effective upgrades. You shall produce new systems and updates to the hardware and software. Other responsibilities include writing system guidelines, training others to use the system, monitoring the system installations, and examining them for further issues.
4. Computer Network Architect
Computer network architects create local, substantial areas and various data interaction networks. They shall update software and hardware, strategize the networks they want to create and show the plans to other members, find new technology helpful for the agency, analyze the networks for issues, and adopt ways to eradicate the same.
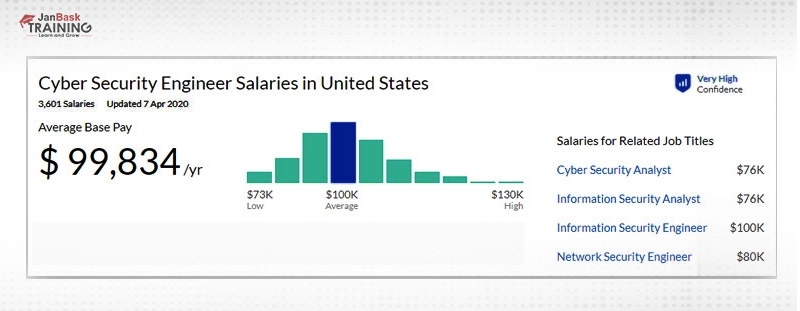
What is the Average Salary for Cybersecurity?
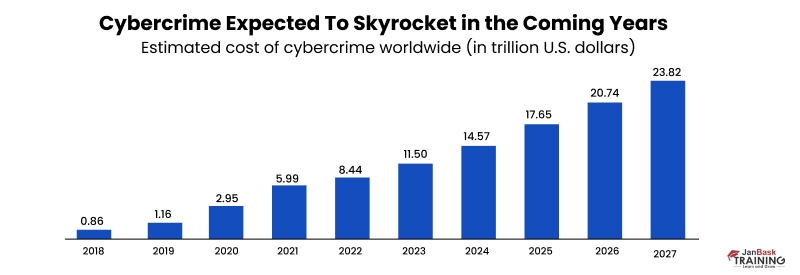
With the rise in cybercrime, there is an unsurprising corresponding increase in demand for information security or cybersecurity professionals. Not only do opportunities abound, but also offer solid job security with generous compensation.
Here’s a sample of popular cybersecurity job roles with their average salary range:
- Information Security Manager: $125,000 to $215,000
- Cybersecurity Engineer:$120,000 to $200,000
- Application Security Engineer: $120,000 to $180,000
- Cybersecurity Analyst: $90,000 and $160,000
- Penetration Tester: $80,000 to $130,000
- Network Security Engineer: $125,000 to $185,000

How to be a Cybersecurity Professional with no Experience?
Absolutely. A formal degree isn’t your only ticket into the world of cybersecurity—what really matters is relevant certifications, hands-on training, and the right mindset.
It may sound surprising, but many professionals have successfully launched cybersecurity careers without a tech degree. In fact, with the industry facing a severe shortage of skilled professionals, companies are increasingly open to hiring candidates who can prove their expertise through practical skills and certifications.
According to the latest U.S. Bureau of Labor Statistics data, jobs for information security analysts are projected to grow by 32% from 2022 to 2032, much faster than the average for all occupations.
So what’s the catch? Employers still need proof that you can deliver. While a degree can help, earning a recognized cybersecurity certification and gaining practical experience through platforms like JanBask Training can be just as powerful—if not more so.
If you're someone coming from a non-technical background and wondering how to break in, check out this helpful guide: How to Transition into Cybersecurity from a Non-Tech Background
With the right training, certification, and mindset, you can confidently step into one of the most in-demand and rewarding careers today.
Cyber Security Training & Certification
- No cost for a Demo Class
- Industry Expert as your Trainer
- Available as per your schedule
- Customer Support Available
Conclusion:
Whether information security and cybersecurity both deals with data protection but differs in the breadth of their focus. Both are the two most demanding traits as they are complementary to each other. Become the part of the JanBask Training Community to get connected with the top industry professionals and cyber experts.
As cyber threats become a growing reality for businesses, organizations need to prioritize developing and maintaining a team of highly trained Information security or cybersecurity experts. Such security solutions help an organization monitor, detect, report, and counter cyber threats to maintain data and information confidentiality. This growing demand for cyber security professionals opens up the door for those who want to become security professionals. All you need is to polish your skills, get a relevant degree and certifications.
Did you enjoy this blog article? Comment below
Frequently Asked Questions
Q1. What are the benefits of the cyber security training & certification course?
Ans: Cyber security training & certification course is crucial as it proves and verifies an individual’s cybersecurity knowledge, capabilities, and professionalism. The cyber security training course also allows people to stand apart from the rest of the crowd in the job scenario and support them in their career path with extra confidence.
Q2. What are the various career paths that one can dream of on attending cyber security training?
Ans: Cybersecurity training is necessary to advance in this domain. It validates your knowledge and introduces you to various new terms related to the concept. The cyber security training course leads to different careers, such as chief information security officer. Security architect, cybersecurity engineer, malware analyst, and many more.
Q3. What are the prerequisites needed to take up the cyber security training online?
Ans: There are particular prerequisites to taking up cyber security training online. An individual must have a bachelor's degree in technology in cyber security. Also, the candidate must have passed his 10+2 with subjects including Physics, Chemistry, and Maths.
Q4. What are the subjects included in the cybersecurity training classes?
Ans: The cybersecurity training classes include business intelligence, data security, risk analysis, penetration testing, network security, and others.
Q5. Are cybersecurity training classes difficult for freshers?
Ans: The cybersecurity training classes are tough to learn. However, like other domains, the candidate must be interested in learning cybersecurity. A detailed comprehension of networking is needed to begin a career in this domain. It will enable you to know the data transfer’s technical dimensions, which will protect the sensitive data.
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
7 days 25 Jul 2025
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
-0 day 18 Jul 2025
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
5 days 23 Jul 2025
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
7 days 25 Jul 2025
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
7 days 25 Jul 2025
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
-0 day 18 Jul 2025
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
1 day 19 Jul 2025
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
-0 day 18 Jul 2025
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
7 days 25 Jul 2025
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
-0 day 18 Jul 2025
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
7 days 25 Jul 2025
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
-0 day 18 Jul 2025



























Paxton Harris
Earlier I thought both are the same but thanks to this blog now I am able to differentiate between them.
JanbaskTraining
Hello, JanBask Training offers online training to nurture your skills and make you ready for an amazing career run. Please write to us in detail at help@janbasktraining.com. Thanks!
Harry
Is it necessary to have a science background to grow a carrier in cybersecurity?
JanbaskTraining
Glad you found this useful! For more such insights on your favourite topics, do check out JanBask Training Blogs and keep learning with us!
Louis Anderson
From where I can get a security clearance?
JanbaskTraining
Thank you so much for your comment, we appreciate your time. Keep coming back for more such informative insights. Cheers :)
Phoenix Robinson
Well-written blog, helpful for professionals who want to plunge into a cybersecurity career.
JanbaskTraining
Thank you so much for your comment, we appreciate your time. Keep coming back for more such informative insights. Cheers :)
Paul Wilson
I am preparing for the last two years but unfortunately not cleared certification. I am really willing to join this career, please guide me on how to prepare well.
JanbaskTraining
Thank you so much for your comment, we appreciate your time. Keep coming back for more such informative insights. Cheers :)
Paxton Harris
I am interested in building my career in Information Security. Can anyone help me with that?
JanbaskTraining
Glad you found this useful! For more such insights on your favourite topics, do check out JanBask Training Blogs and keep learning with us!
Josue Rodriguez
Can I learn both Information security and Cybersecurity?
JanbaskTraining
Glad you found this useful! For more such insights on your favourite topics, do check out JanBask Training Blogs and keep learning with us!
Bradley Thompso
Hi! Informative blog, can you share some links related to the certifications so that I can prepare for them efficiently?
JanbaskTraining
Glad you found this useful! For more such insights on your favourite topics, do check out JanBask Training Blogs and keep learning with us!
Colin Rodriguez
What is the cost of the Selenium tester course at your institute?
JanbaskTraining
Glad you found this useful! For more such insights on your favourite topics, do check out JanBask Training Blogs and keep learning with us!
Arlo Hill
As I am doing b.tech in computer science, planning to grow my career in automation testing, from where I can start, do I need to join any additional courses to learn automation testing?
JanbaskTraining
Thank you so much for your comment, we appreciate your time. Keep coming back for more such informative insights. Cheers :)
Nash Martin
Can you help me with my security clearance? I have no idea how to do it.
JanbaskTraining
Thank you so much for your comment, we appreciate your time. Keep coming back for more such informative insights. Cheers :)
Simon Martinez
Nice blog! Now I am clear in my mind which one to choose between Information security and Cybersecurity?
JanbaskTraining
Thank you so much for your comment, we appreciate your time. Keep coming back for more such informative insights. Cheers :)
Lane Clark
How much does it cost to pursue an Information security course from your institute?
JanbaskTraining
Thank you so much for your comment, we appreciate your time. Keep coming back for more such informative insights. Cheers :)