Introduction
Once in a lifetime, we all have to undergo the crossroads of making a necessary decision about our career path. It is a common scenario in everyone’s life and undoubtedly the turning point of a person’s life. If you are experiencing the same and need clarification in choosing the relevant career path, this blog will help you decide.
With the increased reliance on technology across all sectors of our lives, understanding the distinction between these two tech-related topics is important. In this blog post, we'll break down both concepts to give you a clearer understanding of what is cloud computing versus cyber security. Learn why it's essential to have knowledge about each one and how they play a crucial role in today's global digital network.
Cloud Computing and Cyber Security: Definitions
Cloud Computing delivers various services over the Internet, comprising servers, stores, storage, networks, and analytic data. Organizations choose cloud computing to decrease costs and enhance scalability. It is a method for sustaining continuity even in periods of fast growth.
Here are some Cloud Computing Services that you should know about:

- Software as a Service (SaaS): This application service is offered over the cloud. Businesses widely use this to distribute their apps to end users, with a private cloud operated by a third party to maintain the program.
- Platform as a Service (PaaS): A cloud platform service that enables developers to work on their apps in the cloud. As the organization or a third party maintains the server, storage, and networking, managing their development is more accessible and enables them to concentrate entirely on development.
- Infrastructure as a Service (IaaS): It provides businesses with an entire operational infrastructure, including private cloud-based networking, storage, and other services. This streamlines organizational management procedures and frees up resources that would have been needed in the event of outdated infrastructure.

What is Cyber Security? Cyber security is a set of innovative technologies, services, and procedures to safeguard cloud data, apps, and infrastructure against cyber threats and attacks. For the company to comply with data privacy laws and prevent data loss, robust cloud cyber security is required.
Cybersecurity also denotes the practice of safeguarding the computer and associated devices from online hackers and random people. It comprises various technologies and methods to secure assets and eradicate cyber crimes, including phishing, data breaches, and others security operations center.
Cloud service providers (CSPs) and customers can offer cloud cybersecurity. Most of the time, the CSP also provides its customers access to the newest cybersecurity tools in the cloud, guaranteeing that they have the best protection against well-known online threats like Malware, Ransomware, and other assaults.
Why Cybersecurity is important to you? Data security is a fundamental right of human beings, along with data migrating to a cloud environment. Nowadays, when data is growing exponentially, cloud providers are dealing with more significant risks of data breaches. As the data enhances, so does the attack surface. It is a cloud security solution that is more important than a want.
In case cloud data is compromised, organizations risk loss on various levels, like loss of revenue and reputation. A data breach costs $ 8.64 million, and it takes almost 280 days for a firm to detect, remediate, and recover.
Fun Fact about a Career in Cybersecurity:
In addition, around 80% of organizations globally use the cloud to store their data. What’s more, about 82% of firms reported saving money when they adopted the cloud, and 14% reported laying off their IT department as an outcome of the presence of the cloud.
How do cyber security and cloud computing preserve the security of personal data?
Many users will use the cloud to increase their phone’s storage capacity. However, many individuals are concerned about the safety of the pictures they have shot over time.
The cloud can ensure security by excluding traffic attempting to access data stored in the cloud. It also filters out the traffic by letting authorized users access information while blocking unauthorized access. The traffic is then sent directly to the cloud rather than passing via other servers that could collect its users’ data.
Cybersecurity, on the other hand, approaches security uniquely, involving consumers actively adopting security precautions to safeguard their data.
Also, Cybersecurity can be maintained:
- Avoid opening any strange links in emails, especially personal ones, since they frequently contain emails that appear to be from a reputable organization. These URLs might take you to Malware or request personal data.
- Cybersecurity protects your data by using strong passwords and often updating them. Malware can steal your credentials if it has access to your computer system.
- Setting up two-factor authentication protects your data while validating a different code each time you connect to an account might be annoying. Users will receive a text message if someone other than themselves tries to log into their account, in addition to the fact that it is more difficult to access.
Cloud Computing vs Cybersecurity: Differences

Below you can go through the Cloud computing and Cybersecurity differences in brief:
Liability
Cyber security is vital because people must accept precautions to protect devices from Malware that could steal their data. Cybersecurity protects your devices from being hacked by leaving your users vulnerable to private data being stolen and sold on the dark web.
Hackers have accepted their methods to access the cloud since many people have used it. Cloud service providers deploy technological protection to prevent data theft or the leaking of personal information. Additionally, cloud services are used extensively worldwide.
However, companies must safeguard the security and privacy of cloud customers’ data since failing to do so might expose them to significant liability. So, cloud security is necessary while keeping personal data there.
Responsibility for the security
With Cybersecurity, it is generally the device owner’s responsibility to maintain the safety of private personal information. Then, you are responsible for monitoring your information. It is also the device owner’s responsibility to maintain Cyber security to protect their data from hackers.
Cloud Security is monitored by the vendors serving the software instead of the individual who owns the device.
The API, i.e., the Application Programming Interface, also causes it to be more automated. Since it is Automated, the responsibility of maintaining the security of users’ information is less reliant on humans, so human error is less likely to occur.
Data Access
In Cloud Security, there are two types of data storage in cloud platforms- public and partitioned.
- Public Cloud- The data is stored in public cloud platforms accessible by users without any region restrictions. In contrast, some data stored on the platform might be only reachable to restricted areas due to compliance with laws and regulations.
- Partitioned Cloud- Data stored on this cloud platform is divided so that one user’s data isn’t reachable to other users. It also depends on business needs and which kind of cloud platform may be opted for by firms.
In Cybersecurity, it can be used by both cloud service providers and the customers themselves. It doesn’t have access to the data stored on the cloud platform. The protection is only provided to the network from viruses, Malware, etc.
Prevalence of Each Security
Cloud Security is used by all countries globally, comprising the public sector, private sector, and NGOs. Because of its effective performance, it has become popular among organizations serving cloud computing services.
In Cybersecurity, users or organizations must follow separate security policies based on each country’s cyber policy.
Detection of Security Threats
Traditional cybersecurity techniques use antivirus software to identify and reduce security risks. The issue with employing antivirus products is that they frequently fall behind evolving threats and demand immediate upgrading to stay up with hacker strategies. On the other hand, traditional cybersecurity techniques increase the chance of an attack on people’s devices.
Threats are determined by Cybersecurity signatures, eliminating any lag caused by traditional cybersecurity software. Signatures in cloud security define threats, so there is no lag.
Cloud computing utilizes artificial intelligence (AI) to detect and recognize threats impulsively. It doesn’t need any updates, such as the traditional methods used. Moreover, Artificial Intelligence stays on top of the hackers’ methods so they are more protected from cyber-attacks. Also, it decreases the risk of one occurring is lower.
Data Backup
Because you can see who is accessing your data, some individuals think using standard cyber security backups is preferable, but these backups may be labor-intensive and expensive. You or an IT professional must maintain a regular backup schedule.
Also, more storage must be purchased so these backups can be stored easily. Data can be lost permanently if this doesn’t happen; hence regular backup maintenance is needed.
Because they are automated rather than manual, cloud security backups differ from regular cyber security backups. A vendor automatically manages backups; an IT professional is not responsible for them. As a result, cloud security backups are far less expensive than conventional cyber security backups.
This means you wouldn’t have to purchase more computer storage for backups. iCloud can buy more iCloud storage, which is considered an expensive process as storing data through these methods depends on their proximity.
Data Storage
People who choose to store data through these methods may often be more satisfied because it can control how things are organized.
The ability to choose who can access their data and who cannot makes these approaches more popular with users. A lot of human responsibility is included, so it is easier for human error to spoil the data storage security. As a result, there is a greater chance that data will be compromised.
Cloud security does not store data onsite. This means there is less risk of data going through physical harm since it is harder for people to access the cloud. Many cloud service providers have highly technical and secure data centers to protect your data from cyber threats.
Benefits
You must be aware of the advantages of each type of security if you want to be sure you are protecting your data in the best possible way.
Cloud Security is beneficial for keeping data safe for the following reasons such as:

- Security: Keeping threats away from the business.
- Protection: Reducing the possibility of data and information loss.
- Recovery: Ensuring that deleted data is avoided.
- Affordability: Low cost of infrastructure investment.
- Outsourcing: Instead of you, a third-party provider is in charge of security.
While Cybersecurity allows you to tailor your protection to your preferences, cloud security requires less of a risk of regular people making mistakes. Additionally, it offers you the desired amount of protection.
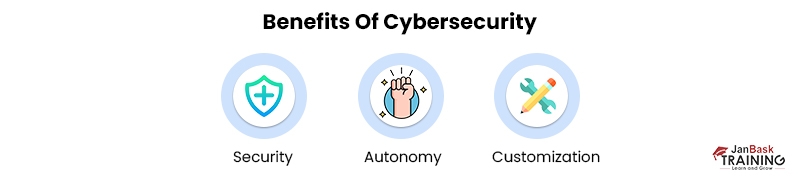
Here are some benefits of cybersecurity that you should know:

- Security: Both Physical and network security are served
- Autonomy: You continue to have control over your data and what happens to it.
- Customization: Configure the system on your device to your preferences.
Required skills
Take a look at the skills needed to become a cloud computing professional.


- Database ideas: Cloud experts must have basic knowledge of database platforms.
- Programming skills: They must have an idea about one programming language.
- Operating systems: They should have good experience with one operating system.
- IT security concepts: Cloud experts must know IT security concepts that frame and present a proper infrastructure in IAAS models.
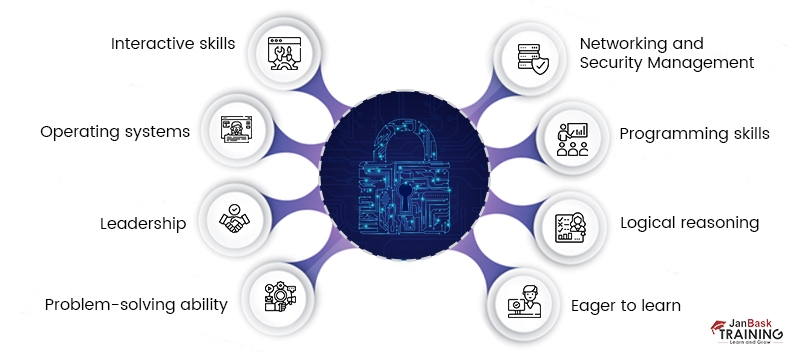
Skills to become a cybersecurity expert are as follows:

- Networking and Security Management: Cybersecurity experts must have proper network and system management capacity to work on multiple networking layers.
- Programming skills: Good programming skills are mandatory in C, C+ +, PHP, Java, Python, and others.
- Logical reasoning: The individual must have the potential to reason and realize the cyber security problems by putting the best technical ways into practice.
- Eager to learn: The expert should be anxious to learn unknown concepts rapidly.
- Interactive skills: Cyber Security experts must possess healthy verbal and written interactive capabilities to communicate the related issues and handle the same collaborating with the other teams.
- Operating systems: They should possess working experience in various operating systems like Windows and Linux.
- Leadership: Potential to lead the team
- Problem-solving ability
Drawbacks
You may choose the finest security method for your data by being aware of the drawbacks of each type of protection. Although cloud security is less of a human responsibility, there are still several drawbacks, including:
Systems could be pre-configured, making it impossible to modify them if you don’t like them.
- Loss of control over the operation of the security
- If a natural disaster occurs, data loss might ensue
- Backups and restores might take longer
- Increased usage of the Internet
In contrast to cloud security, there are far fewer duties that you must assume when it comes to cyber security. Cybersecurity can be essential to keeping your data secure; however, there are also multiple cons to it, such as:
- It can be a challenge to install a firewall correctly
- Few cybersecurity programs can make the computer system a bit slower
- Constantly needed to update the settings to ensure they are up to date
- Its programs can be very costly
- You are responsible for managing the security
Take A Leap: Cloud Computing vs Cyber Security

Cloud Computing and Cyber Security: Career
In this section, we will see the career outlook for cloud computing and cybersecurity.
If you like hacking, explaining bugs, and making the web world more secure, then cyber security is well-versed for you; if you're looking for something more associated with data availability and accessibility rather than security, then Cloud computing is the right field for you. In this section, we will see the career outlook for both.
Career In Cloud Computing
Multiple companies are shifting to the cloud, and the field of cloud computing is increasing. Considering the flow of data and its complexities, cloud computing is seen as a savior by organizations struggling with data storage and handling issues.
It offers computer solutions over the Internet. Moreover, to excel in this field, one must have a good command of concepts such as databases, networks, and software programming.
The three main subcategories of cloud computing— Platform as a Service (PaaS), SaaS (Software as a Service), and IaaS (Infrastructure as a Service)— are discussed above. If you enjoy hacking, debugging flaws, and making the web safer, then cyber security is the area for you; if you prefer something more related to data availability and accessibility rather than protection, cloud computing is the sector for you. An individual needs solid foundations, good practical knowledge, and the capacity to stay up with cutting-edge technology to have a successful career in cloud computing. Despite this, individuals require certification in cloud computing-related courses for better opportunities.
Note: With decreasing local centers and a rise in the use of cloud platforms, we can be sure that cloud computing is staying on the trending list for a while.
Career In Cybersecurity
Coming to the Cyber security career path, we must consider the prerequisites to make a successful career in this field. Cybersecurity is something that is and should be thought of as a ladder. As is, the parent encompasses far too many domains. When someone is familiar with the principles of these components, they have a basic understanding of Cybersecurity.
One should have in-depth knowledge and comprehension of technological fields like computer networking before working on cyber security. Computer networking includes the working of switches, routers, subsets, IP, and so on. The domains secured by Cybersecurity are Web App Security, IoT security, Network security, etc. Then, knowing a few programming languages, such as Python or Java, is necessary.
Note: The most crucial prerequisite here is understanding the working of the Linux platform. Opting for these three subfields forms the groundwork for cyber security as a career option.
Cloud Computing and Cyber security: Job opportunities
Job opportunities in cyber security
The reach of cyber security in India is rising because, nowadays, everything is getting technology-oriented, and the chances of internet hacks are increasing. Regarding employment prospects in Cybersecurity, an OSCP (offensive security certified professional) certification is required to get hired as a cybersecurity analyst. Salary is an intuitive question, but cyber security analysts earn more than 6LPA in the initial years.
The various job titles in cyber security with their respective salaries have been listed below:
- Chief security officers - $145,000 to $248,000
- Data security analysts - $102,000 to $171,500
- Systems security experts - $92.750 to $ 156,00
- Network security engineers - $92,000 to $155,000
Job opportunities in cloud computing
Cloud computing is considered a savior by companies who find it difficult to store data. The extent of cloud computing is elevating since most companies are transferring their data to the cloud. To outshine cloud computing, an individual should have a good knowledge of databases and networks. The candidate requires certification in cloud computing courses for more opportunities.
Cloud Computing and Cyber Security: Salary
Cybersecurity is one of the most lucrative jobs in the USA. One needs to possess proper interactive capacities and flexibility in handling modern technologies. The average salary of a cyber security expert in the USA is $57.57 per hour.
Per Payscale salary details, the average network security analyst salary is $72,388, whereas the average cybersecurity analyst salary is $76,550. Since both Cloud Computing and Cyber Security professionals are equally demanding, the difference between cyber security professional salary and cloud solutions engineers is even narrower, with the former earning $87,016 on average and the latter at $87,246.
What To Choose For Your Next Project: Cloud Security Vs. Cybersecurity?


Cloud Security: It is used by almost every firm and person to store their data safely in the cloud. It has become a modern technology because of its effective performance compared with traditional means such as paper, hard disks, etc.
Cybersecurity: The security method is chosen by cloud security or Cybersecurity based on the security level required by a firm or person. Cloud security is much more efficient in its working compared to Cybersecurity, but it is a bit expensive compared with the latter. Moreover, Cyber security refers to the accumulation of modern security techniques which assures total security for a company. Cybersecurity is of prime vitality for physical security because the entire world is using the internet.
Conclusion
There is no denying that cloud computing is the future trend and that Cybersecurity will remain a top priority. Together, these factors show that cloud security is the next step in IT growth as data volume and risk increase, legislation like GDPR makes security enforceable, and new IoT technologies undermine it. So maintain your cloud security by being knowledgeable, ensuring you or your personnel are educated, and maintaining a healthy degree of mistrust by choosing the best cybersecurity certification.
AWS Course
Upcoming Batches
Trending Courses
Cyber Security
- Introduction to cybersecurity
- Cryptography and Secure Communication
- Cloud Computing Architectural Framework
- Security Architectures and Models
Upcoming Class
15 days 03 Oct 2025
QA
- Introduction and Software Testing
- Software Test Life Cycle
- Automation Testing and API Testing
- Selenium framework development using Testing
Upcoming Class
4 days 22 Sep 2025
Salesforce
- Salesforce Configuration Introduction
- Security & Automation Process
- Sales & Service Cloud
- Apex Programming, SOQL & SOSL
Upcoming Class
1 day 19 Sep 2025
Business Analyst
- BA & Stakeholders Overview
- BPMN, Requirement Elicitation
- BA Tools & Design Documents
- Enterprise Analysis, Agile & Scrum
Upcoming Class
1 day 19 Sep 2025
MS SQL Server
- Introduction & Database Query
- Programming, Indexes & System Functions
- SSIS Package Development Procedures
- SSRS Report Design
Upcoming Class
1 day 19 Sep 2025
Data Science
- Data Science Introduction
- Hadoop and Spark Overview
- Python & Intro to R Programming
- Machine Learning
Upcoming Class
8 days 26 Sep 2025
DevOps
- Intro to DevOps
- GIT and Maven
- Jenkins & Ansible
- Docker and Cloud Computing
Upcoming Class
-1 day 17 Sep 2025
Hadoop
- Architecture, HDFS & MapReduce
- Unix Shell & Apache Pig Installation
- HIVE Installation & User-Defined Functions
- SQOOP & Hbase Installation
Upcoming Class
8 days 26 Sep 2025
Python
- Features of Python
- Python Editors and IDEs
- Data types and Variables
- Python File Operation
Upcoming Class
2 days 20 Sep 2025
Artificial Intelligence
- Components of AI
- Categories of Machine Learning
- Recurrent Neural Networks
- Recurrent Neural Networks
Upcoming Class
16 days 04 Oct 2025
Machine Learning
- Introduction to Machine Learning & Python
- Machine Learning: Supervised Learning
- Machine Learning: Unsupervised Learning
Upcoming Class
29 days 17 Oct 2025
Tableau
- Introduction to Tableau Desktop
- Data Transformation Methods
- Configuring tableau server
- Integration with R & Hadoop
Upcoming Class
8 days 26 Sep 2025